Table of Contents
- Creating Hyper-V Virtual Switches
- Configuring Virtual Switch in Hyper-V using Hyper-V Virtual Switch Manager
- Private Virtual Switch
- Internal Virtual Switch
- External Virtual Switch
- Creating Hyper-V Virtual Switches with PowerShell
- Concluding Thoughts
In the previous post, we looked at the overview of Hyper-V virtual switches and saw the architecture of the virtual switch in the realm of Hyper-V as well as its capabilities, features, and functionality within the Hyper-V environment.
Creating and managing Hyper-V virtual switches is a necessary component of managing and maintaining your Hyper-V infrastructure.
In this second part of the Hyper-V virtual switch overview, let’s take a look at the steps to create Hyper-V virtual switches using Hyper-V Virtual Switch Manager and Powershell.
Creating Hyper-V Virtual Switches
Hyper-V standard virtual switches can be created using either the Hyper-V Manager GUI or by using PowerShell.
We will take a look at each of these methods of configuration and deployment to see how the standard Hyper-V virtual switch can be deployed using either method.
Configuring Virtual Switch in Hyper-V using Hyper-V Virtual Switch Manager
Open Hyper-V Manager and choose the “Virtual Switch Manager” option.
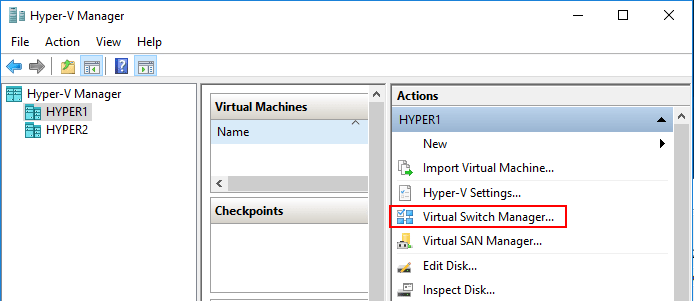
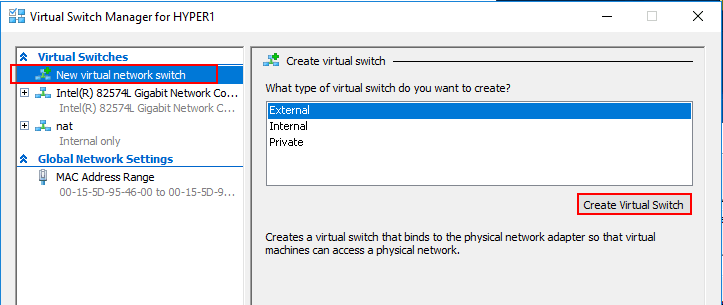
In the Virtual Switch Manager wizard, choose the “new virtual network switch” option and select the type of virtual switch you want to create.
Private Virtual Switch
The virtual switch that only allows communications between the connected virtual machines that are connected to the private virtual switch.
Internal Virtual Switch
The Internal Virtual Switch only allows communication between virtual adapters connected to connected VMs and the management operating system.
External Virtual Switch
The External virtual switch is connected to a physical network adapter that is installed in the Hyper-V hosts which makes this communication outside the host possible.
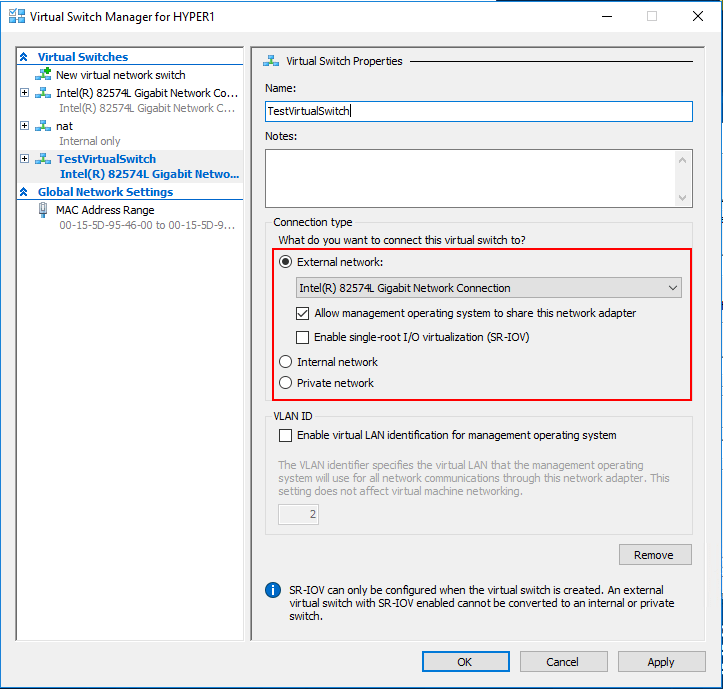
Looking at the Hyper-V virtual switch properties, you can set the Connection type as well as the VLAN ID for the new Hyper-V virtual switch.
Creating Hyper-V Virtual Switches with PowerShell
Using PowerShell for virtual switch creation is a great way to achieve automation in a Hyper-V environment. PowerShell makes it easy to create new Hyper-V virtual switches in just a few simple one-liner cmdlets.
- Get-NetAdapter– make a note of the names and network adapters
- External Switch – New-VMSwitch -name < switch name > -NetAdapterName < network adapter name > -AllowManagementOS $true
- Internal Switch – New-VMSwitch -name < switch name > -SwitchType Internal
- Private Switch – New-VMSwitch -name < switch name > -SwitchType Private
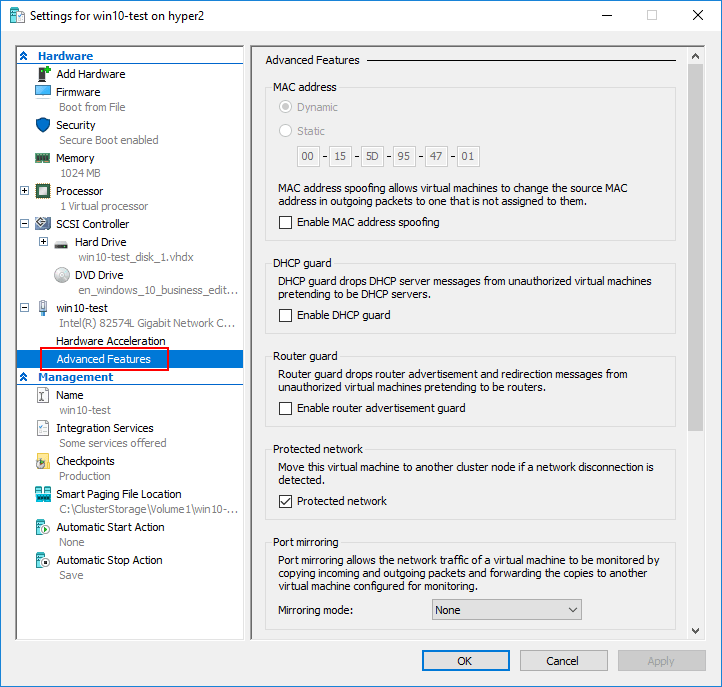
While not directly related to the Hyper-V virtual switch configuration, the virtual machine level Advanced Features include several very powerful network features made possible by the Hyper-V virtual switch including:
- DHCP guard – Protects against rogue DHCP servers
- Router guard – Protects against rogue routers
- Protected network – A high availability mechanism that ensures a virtual machine is not disconnected from the network due to a failure on a Hyper-V host
- Port Mirroring – Allows monitoring traffic.
Concluding Thoughts
Creating and managing Hyper-V virtual switches is a critical administration task that Hyper-V administrators need to perform to run production workloads in a way that allows connectivity in the desired way and to manage your Hyper-V environment effectively. Thus, it’s clear that Hyper-V Virtual Switch is an integral part of Hyper-V hypervisor that makes virtualization and virtual connectivity possible.
In the next part of the series, we will take a look at how to manage Hyper-V virtual switches, through the GUI and programmatically.
Related Posts
Hyper-V Virtual Switch – Part 3 – Managing Hyper-V virtual switches
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

