When it comes to any IT infrastructure today, one of the chief concerns for organizations and administrators alike is security. Today’s modern hypervisor solutions that power most of today’s enterprise data center environments have powerful security features that are built into both the host as well as the virtual machines that run on top of the hypervisor. Windows Server 2016 Hyper-V has really great security features from a virtual machine perspective that allow Hyper-V administrators to provide an extremely secure solution for business-critical production workloads.
Let’s take a look at Windows Server 2016 Hyper-V Virtual Machine Security Features and how these built-in features allow organizations to secure the virtual machines that run critical applications and services that power their businesses.
What features does Windows Server 2016 Hyper-V provide to Hyper-V administrators for securing virtual machines? How are these features implemented?
Windows Server 2016 Hyper-V Virtual Machine Security Features
With Windows Server 2016, certain security features have been enhanced to provide further protection for virtual machines that are running on top of Windows Server 2016 Hyper-V.
Let’s look at the following virtual machine specific security features that Hyper-V administrators can implement:
- Virtual Machine Secure Boot
- VM Protection (vTPM)
- Shielded VM
The above features drastically enhance security from a virtual machine perspective in Windows Server 2016 Hyper-V and allow administrators to have much more control over the security stance of their virtual workloads.
Hyper-V Virtual Machine Secure Boot
Today’s servers need to be able to validate the fidelity of the system not simply from an operating system perspective but from the boot process forward. Attackers are getting much smarter and instantiating malware much earlier in the system boot than just the operating system. A mechanism that helps to verify the fidelity of a server is the Secure Boot process.
Secure Boot is built on top of UEFI or Unified Extensible Firmware Interface. UEFI is a much more modern approach than the old legacy BIOS process that booted legacy servers. UEFI, like the BIOS, is responsible for initializing hardware devices before handing control of the hardware devices over to the operating system. However, unlike the legacy BIOS instantiation, UEFI allows features like Secure Boot.
With Microsoft’s implementation of Secure Boot, the operating system can detect rootkits and other malware code that may be attempting to compromise a system during these early initialization phases of a server boot process. This ensures the boot process, all the way from the firmware to the kernel load of the operating system is trusted and has not been tampered with. Secure Boot enforces all boot code and drivers are signed correctly. This greatly minimizes the risk that malware has been instantiated during this phase of the boot process.
Microsoft has brought the Secure Boot process from physical servers into the Hyper-V platform. With Windows Server 2012 R2, the Secure Boot functionality was limited to Windows-based virtual machines. However, with Windows Server 2016, Microsoft has extended support for this security mechanism to supported Linux operating systems running as guest operating systems inside Windows Server 2016 Hyper-V virtual machines.
What are the requirements for Secure Boot in Windows Server 2016 Hyper-V?
- Generation 2 Virtual Machine
- Supported guest operating system (Windows or Linux)
Configuring Hyper-V Virtual Machine Secure Boot
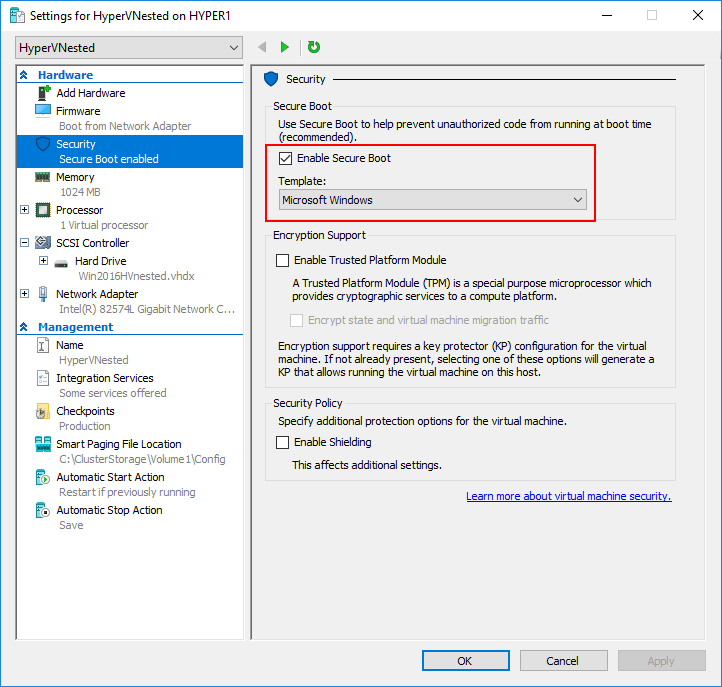
Secure Boot can be enabled from the GUI of Hyper-V manager. PowerShell can be used as well. First, to enable via the Hyper-V Manager console, view the settings for a virtual machine. Click Security and you will see the option to Enable Secure Boot. Place a check by the box to enable it and select the Template for Secure Boot. The template options are:
- Microsoft Windows
- Microsoft UEFI Certificate Authority
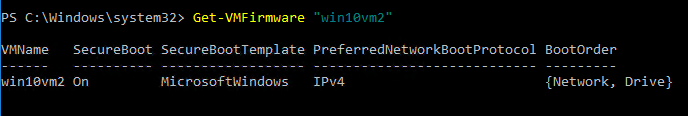
To check to see if Secure Boot is enabled using PowerShell, use the following cmdlet:
Get-VMFirmware “
Secure Boot can be enabled or disabled using PowerShell as well using the following cmdlets:
Windows – Set-VMFirmware “
Hyper-V VM protection (vTPM)
The world of cloud and of enterprise data center computing is by necessity required to have the means to secure data and to establish “trust” in the environment and your data. Trusted Platform Module is a physical device (computer chip) that can store security information that can be used to authenticate your entire platform (workstation or server). The TPM chip generates encryption keys that allow other security mechanisms such as BitLocker to have the ability to use TPM for encryption. Part of the security key is stored in the TPM rather than all of the key being stored on the disk itself. So, TPM raises the difficulty level for an attacker to simply remove an encrypted drive and attempt to break the key at another location because part of the key is stored in the TPM.
However, in the world of virtualization, where virtual machines do not have a physical TPM to interact with, how can this security mechanism be implemented in this use case?
Virtual TPM or “Virtual” Trusted Platform Module does what you think it does – virtualizes the TPM module so it can be utilized by virtual machines. With Windows Server 2016 Hyper-V, the vTPM has been introduced as part of the features of Generation 2 virtual machine that allows using BitLocker to encrypt data on the boot volume of the virtual machine.
There are a few requirements for enabling the vTPM for a virtual machine:
- Windows Server 2016 Hyper-V
- Host Guardian service installed in Hyper-V
- Windows 2012 and above as the guest operating system
First, you install the Host Guardian Service Server Role which can easily be accomplished in Server Manager.
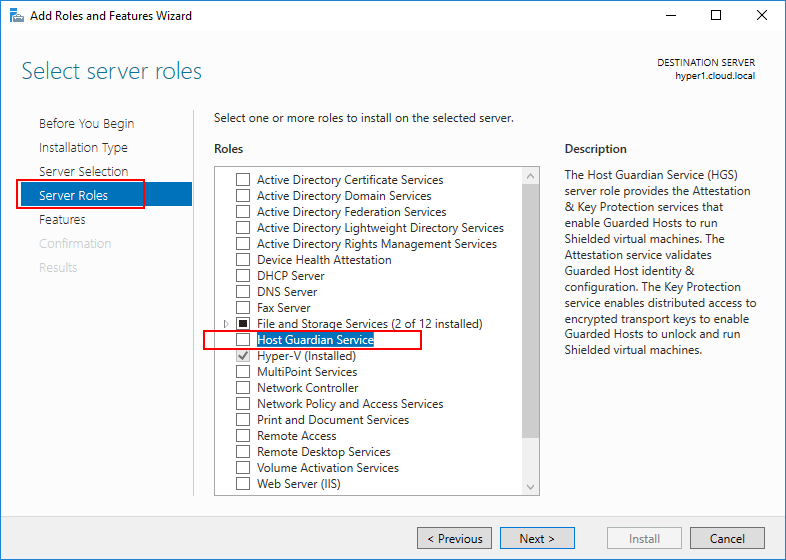
Next through the Add Roles and Features Wizard and Reboot the server once the role has been installed. Now that the prerequisites have been met for vTPM with Host Guardian Service installed on the Hyper-V host, you can enable the vTPM setting on the virtual machine. With the virtual machine powered off, place a check in the Enable Trusted Platform Module checkbox. You can also check the box, Encrypt state and virtual machine migration traffic. Once the virtual machine is powered on and booted, in device manager under security devices you should see the Trusted Platform Module 2.0 listed.
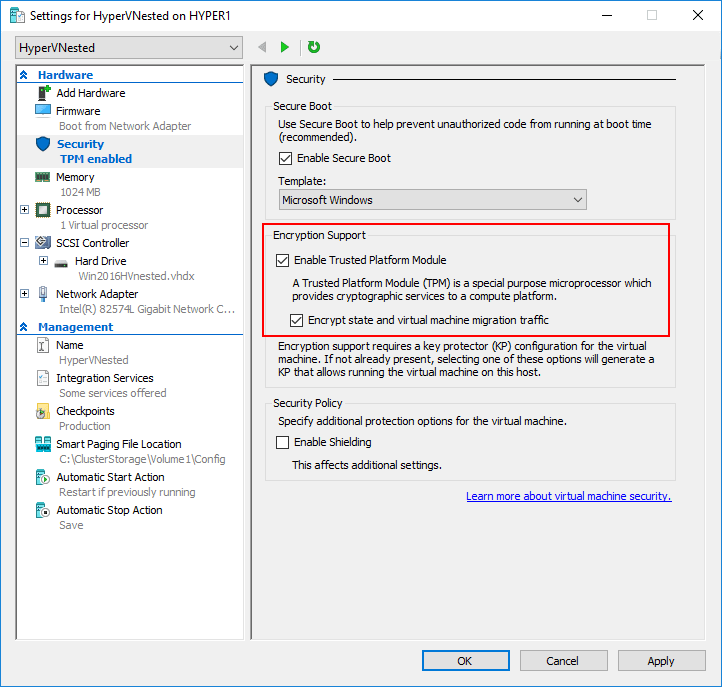
Hyper-V Shielded VM
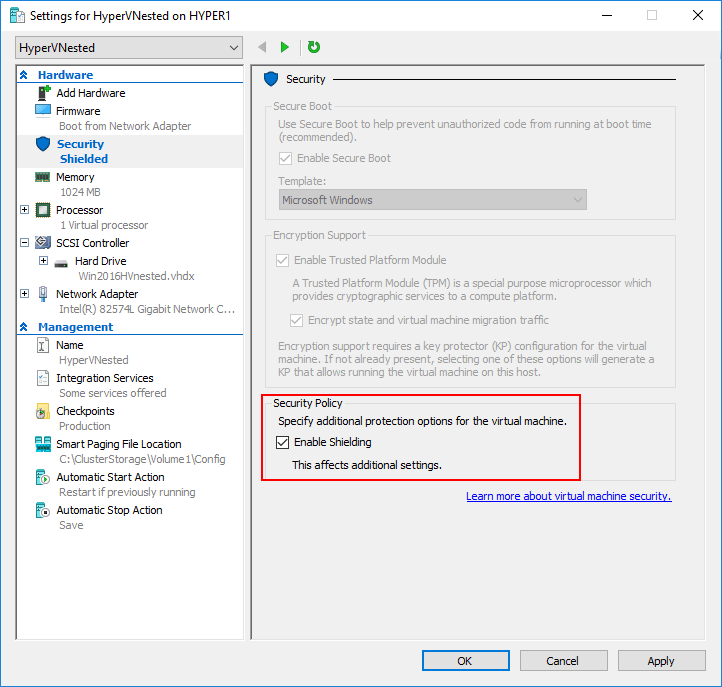
All of the above security settings have thus far been building up to the ultimate security for a virtual machine that Hyper-V can provide – Shielded VMs. With Windows Server 2016, this functionality was introduced. Shielded VMs uses the security functionality provided to Hyper-V virtual machines by the vTPM module that enables encrypting the boot volume and other security-centric features.
Shielded VMs also leverage the Host Guardian Service that was already shown above, however, shielded VMs need to be implemented in production using a true Host Guardian Service configured in a dedicated “at least” three-node cluster running Windows Server 2016 and at least one or more guarded hosts running Windows Server 2016 with Hyper-V. This allows Shielded VMs to run inside of a Guarded Fabric it is called. There are two critical parts of the HGS fabric that perform vital roles in the HGS infrastructure:
- Attestation Service – this checks the health and credibility of the guarded host
- Key Protection Service – this service actually releases the encryption key to power on a virtual machine or perform a Live Migration operation
The Host Guardian Service Guarded Fabric employs a couple of different means for attestation that can be configured:
- Active Directory-Based Trusted – The HGS measures the group membership of the Hyper-V host that it is attesting against
- Trusted Platform Module (TPM) trusted – This is the more rigorous of the two methods and does not require an active directory trust relationship to be present. TPM is leveraged here to provide a unique key which is used by HGS to perform the attestation
You can simply select the Enable Shielding checkbox on a virtual machine, however, it will at that point only use self-signed certificates which does not really make use of a proper HGS certificate chain and would run the risk of having a potentially unrecoverable VM if the private key is ever lost. For production, be sure to follow Microsoft’s guidance to properly set up a Guarded Fabric to properly store encryption keys.
Office Microsoft Shielded VMs documentation
Concluding Thoughts
Windows Server 2016 Hyper-V contains really great new features from a security standpoint that is providing the functionality in the new Hyper-V version to have a good measure of trust in virtual machines running not only on-premises but in the public cloud. From Secure Boot, vTPM, and Shielded VMs, Hyper-V can be configured in such a way that virtual machines are validated and encrypted so as to bolster security and make it exponentially more difficult for attackers to compromise a server.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

