The vSphere Security Configuration Guide (SGC) is a collection of security best practices provided by VMware that used to be known as the Hardening Guide up until vSphere 6.0 and was changed because the number of actual “hardening” settings is decreasing over the releases. Check out our introduction to the SCG here.
VMware recently released the latest version of the Security Guide for vSphere 6.7 Update 1. As always this new version brings its fair lot of changes.
Still more hardening by default
Like every release of vSphere, more and more hardening recommendations that used to be part of the hardening guide are now included out of the box in the code of ESXi. vSphere 6.7 Update 1 takes this figure from 10 down to 5 since vSphere 6.5 Update 1.
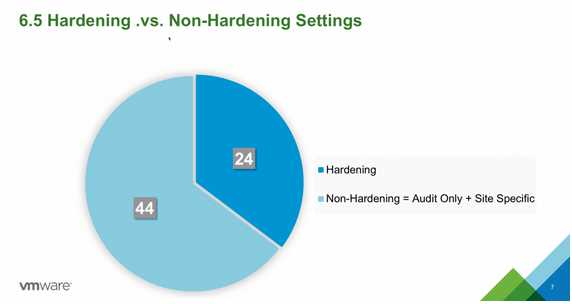


This is great stuff coming from the VMware teams as it means people deploying latest version of vSphere will enjoy a more secure environment from scratch.
Deprecated settings
One of the useful changes that have been brought to the SCG is the “Deprecated settings” category. Any setting listed in this category can be disregarded as they have been fixed in the code of ESXi. They are available in a separate spreadsheet that you can download here, which makes the actual guide clearer, shorter and slicker with now only 50 settings.
Though as Mike Folley from VMware mentions it, you might still want to set these settings on your hosts for auditing purpose if your security policies are that strict.
No more Risk Profiles
Now, for those who have been using the Hardening guide over the years this one will be kind of a biggy. VMware decided to remove the concept of Risk Profiles for the good reason that only one setting would populate the Risk Profile 1. This setting being “ESXi.enable-strict-lockdown-mode“. “ESXi.enable-normal-lockdown-mode” (RP 2, 3) is still the alternative so you still have a choice there.
En route to a fully secure vSphere out of the box?
As you can see, VMware’s objective to offer a fully secured environment out of the box is very obvious. The number of Hardening Settings have dropped dramatically since the early days of the guide and will hopefully keep going down this hill.
Download the latest SCG here and make your environment more secure.
Here are the security recommendations from VMware.


Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

