Table of Contents
- Closer Look at VMware vSphere Virtual Machine Encryption
- How is VMware Virtual Machine encryption implemented anyway?
- How is this helpful in the realm of securing virtual machine data?
- Implementing VMware Virtual Machine Encryption
- VMware VM Encryption Requirements
- Concluding Thoughts
One of the oldest known forms of security is encryption. Encryption generally uses a key of some sort to make data unreadable. Without the key, you can’t read the data. This technology has been used time and time again and has been improved upon by various security technologies and encryption algorithms.
Today’s encryption technology is extremely powerful and is a tremendously effective mechanism in preventing unwanted theft of data. Even if the raw data is stolen, it can’t be read without the proper key to decrypt the data. Virtualized environments have adopted this technology. VMware has implemented the ability to do virtual machine encryption in vSphere 6.5.
In this post, we will take a closer look at VMware vSphere virtual machine encryption configuration, how the technology protects your data and how it is implemented.
Closer Look at VMware vSphere Virtual Machine Encryption
How is VMware Virtual Machine encryption implemented anyway?
VM encryption provides security to the VMDK that stores the data for a virtual machine. The I/O operations are encrypted from a virtual machine before they are written to the VMDK disk. Other files associated with the virtual machine are not encrypted due to their non-sensitive nature. These include the VM log files, configuration files, virtual disk descriptor files, etc.
How is this helpful in the realm of securing virtual machine data?
Imagine the scenario and use case of how this type of security protects your virtualized environment and perhaps, very sensitive data. If an unscrupulous system administrator or someone who has potential access to the VMware vSphere storage copied the virtual machine disk files to a removable device, they could take the disk to another VMware vSphere environment, import the virtual machine disk files into the new environment, power up the virtual machine, and have access to all the data stored on the virtual machine disk file that was copied from the source environment.
Another scenario might involve a domain controller. What if an employee or someone who gained access to VMware vSphere storage was able to copy a domain controller virtual machine to removable storage. They could then perform the same task as above and import the virtual machine into a new VMware vSphere environment, perhaps at home. Then they could run Active Directory password utilities relentlessly against the environment, completely outside the scanning, alerting, and other security mechanisms that might be running on-premises. Passwords can potentially be gathered from the “offline” Active Directory environment and provide an extremely dangerous security situation if this goes undiscovered. The employee could have access to domain admin credentials and potentially impersonate other users, compromising data, stealing data, and even other outcomes.
The above scenarios are only a couple of examples of how unencrypted data can be compromised. Virtual machine disks that are not encrypted are fully readable with no special effort on the part of the attacker outside of having access to the data. Once virtual machine encryption is introduced into the environment, it becomes exponentially more difficult to compromise data, even if you have access to the virtual machine storage.
Implementing VMware Virtual Machine Encryption
So with all the added security benefits to encrypting VMware virtual machines, this is certainly a security feature that most will want to take a look at to secure sensitive virtual machines running in the environment.
Let’s take a look at the requirements and steps to enable virtual machine encryption in VMware vSphere.
VMware VM Encryption Requirements
- Provision a supported Key Management Server cluster to issue encryption keys
- Establish trust between VMware vCenter Server and the Key Management Server cluster
- Change the storage policy to VM Encryption for virtual disks
The process to do this is straightforward and can easily be accomplished via the new fully-featured HTML 5 vSphere client in vSphere 6.7 Update 1.
The first requirement as listed is to provision a Key Management Server cluster.
Most will probably provision a virtual solution running by way of a virtual appliance either in a production or management cluster. The Key Management Server cluster or KMS cluster will most likely be made up of multiple nodes for resiliency and in accord with best practice.
The Key Management Server solution must support the Key Management Interoperability Protocol (KMIP) 1.1 standard to be used as a KMS solution in VMware vSphere. You can find out more about which solutions are supported in the VMware Compatibility Guide.
In the below walkthrough, we will add a supported KMS cluster server solution to the VMware vSphere environment for use with virtual machine encryption tasks.
Navigate to the Configure menu of the vCenter Server inside of the vSphere client. Click Key Management Servers > Add.
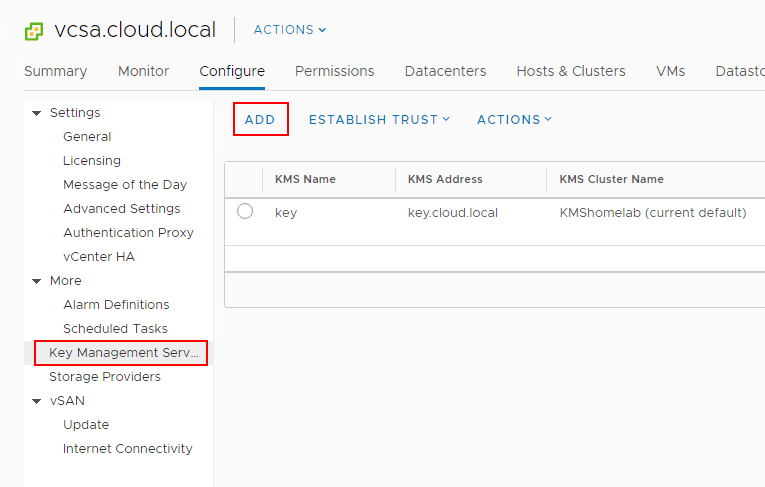
This will launch the Add KMS dialog box that will allow you to Create new cluster or point to an existing cluster. Below we are creating a new KMS cluster inside of the vCenter Server configuration. The process gathers the necessary configuration information including:
- KMS Cluster configuration (create new or point to existing)
- New cluster name with the choice to make the KMS cluster the default configuration
- Server name – This is the friendly name in vCenter Server
- Server address – The IP or FQDN of the KMS cluster
- Server port – port the KMS server is listening on
- Proxy address – (optional)
- Proxy port – (optional)
- User name – (optional)
- Password – (optional)
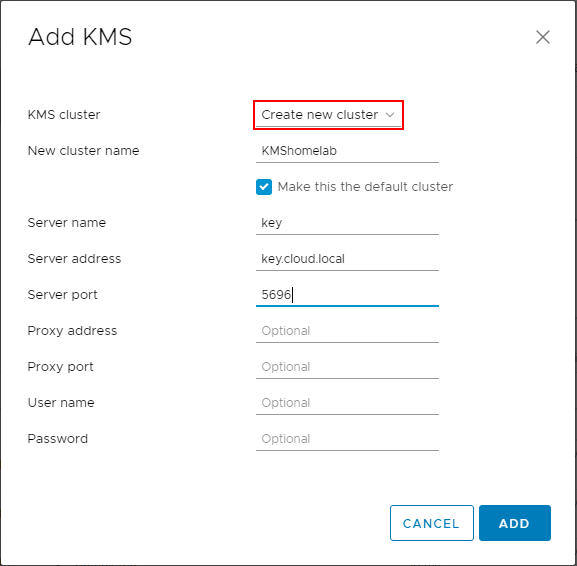
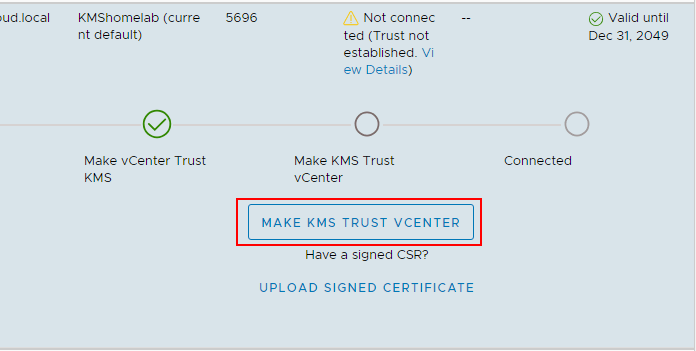
You will see the Make vCenter Trust KMS dialog box open after establishing a connection to the KMS server cluster. Even though you click Trust in this step, there are further steps required for establishing trust in vCenter.
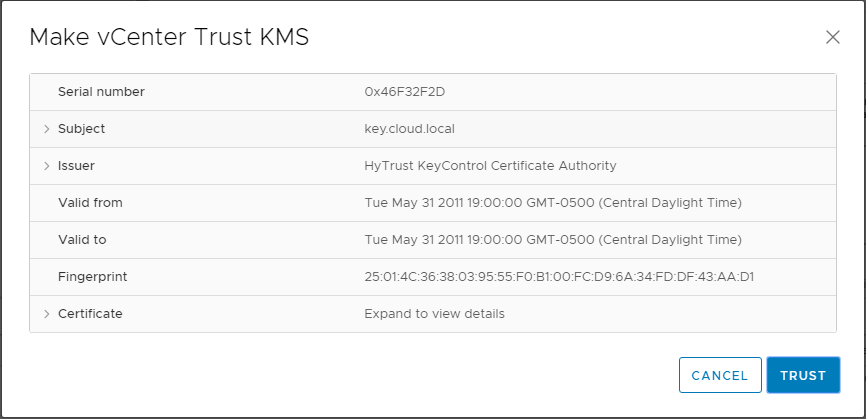
Notice the connection status shows Not connected (Trust not established View Details).
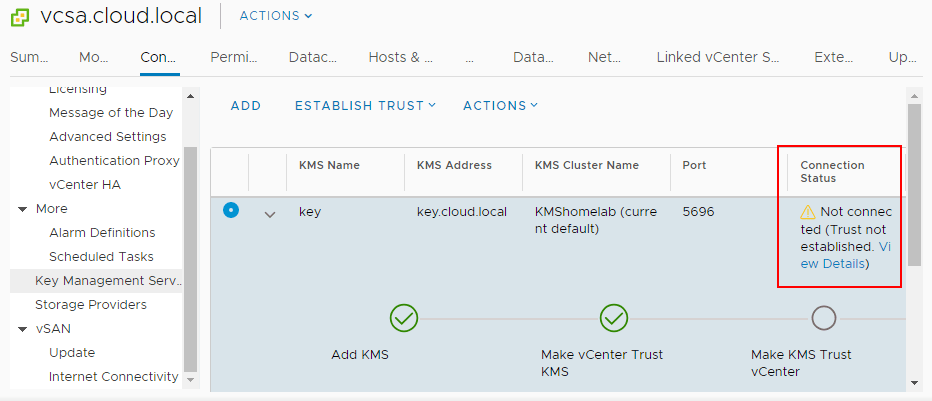
If you click to View Details you will see the MAKE KMS TRUST VCENTER button. Click this button to open the further configuration for trusting the KMS server.
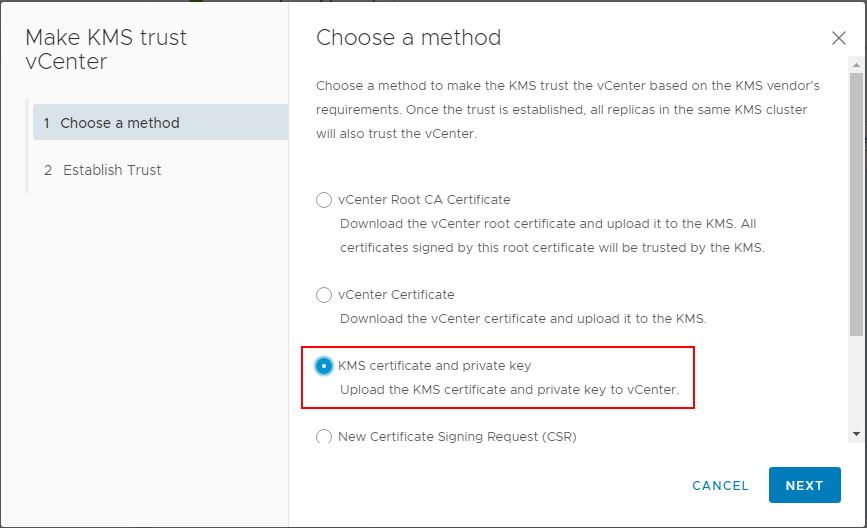
This will launch a wizard to Make KMS trust vCenter with a few options. Since in the lab, I have a certificate downloaded from the KMS server and a private key, I will be uploading these to vCenter for establishing trust.
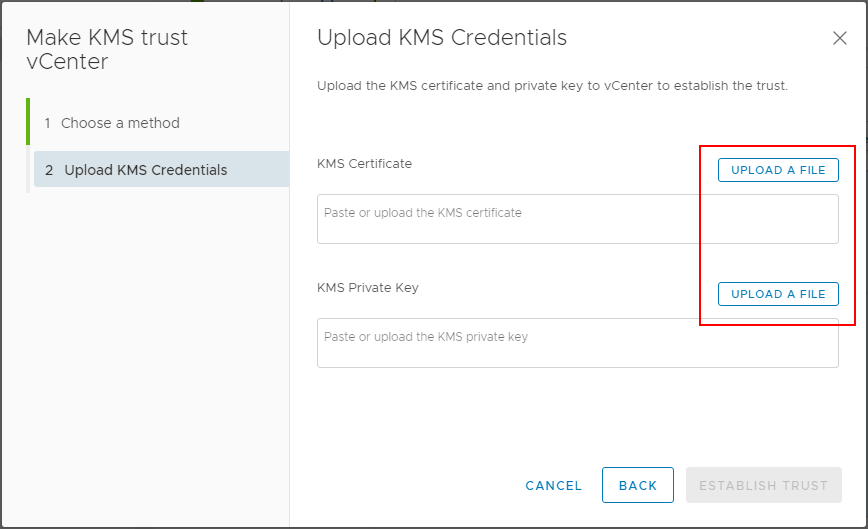
In the Upload KMS Credentials you will see the Upload a file button for both the KMS Certificate and the KMS Private Key.
After uploading the certificate and private key, click the Establish Trust button.
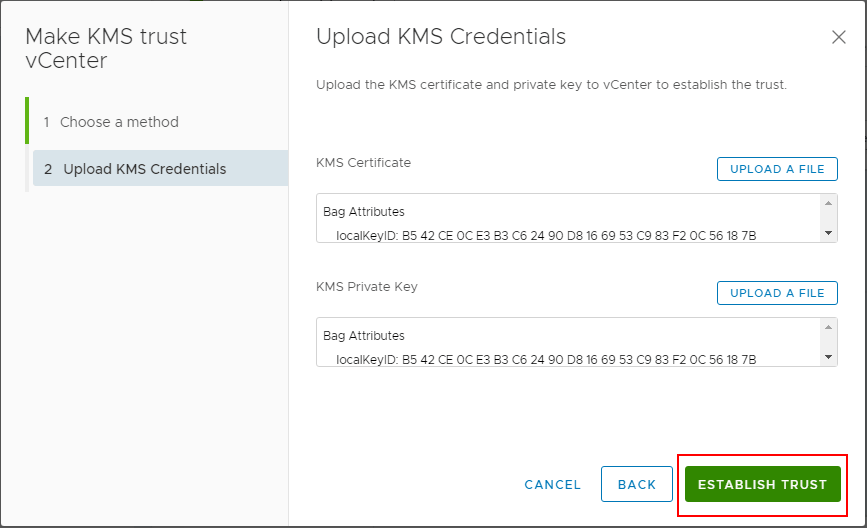
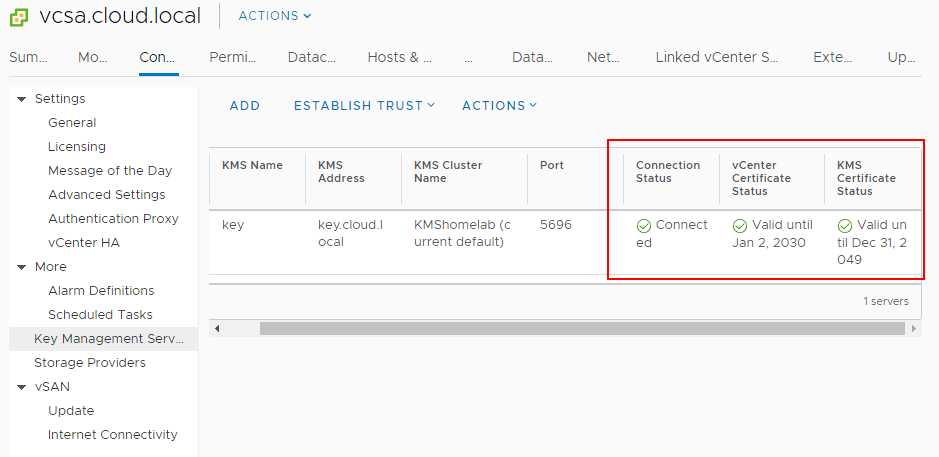
Now, after establishing trust, you will see the connection status, vCenter Certificate Status, and KMS Certificate Status all showing with a green checkmark. Trust has been established.
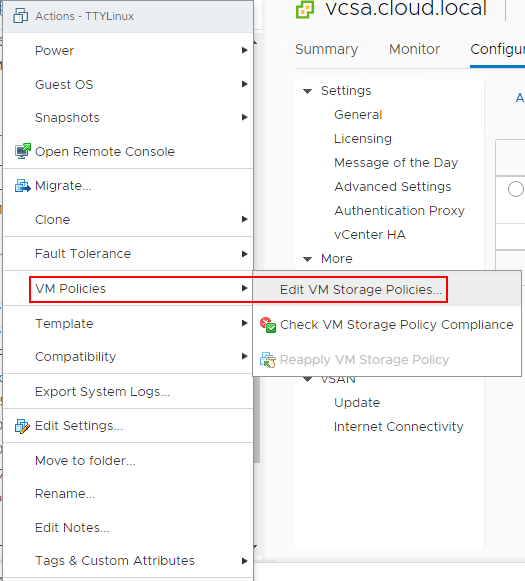
Now that the KMS cluster is in place, we can start encrypting virtual machine disks with the new functionality enabled by the KMS server. To encrypt virtual machine disks, right-click on a virtual machine in the vSphere client inventory, and choose VM Policies > Edit VM Storage Policies.
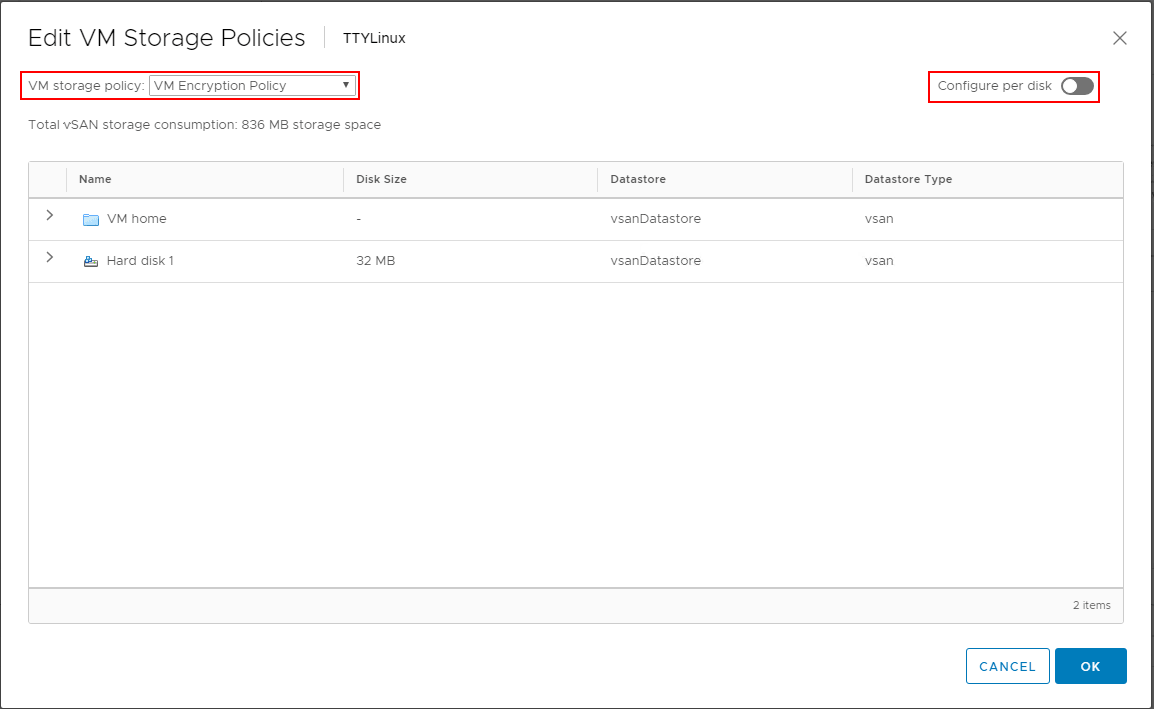
In the Edit VM Storage Policies dialog box, choose the VM Encryption Policy to enable encryption on the virtual machine disk(s). Note how you can granularly assign storage policies, including encryption on a per disk basis.
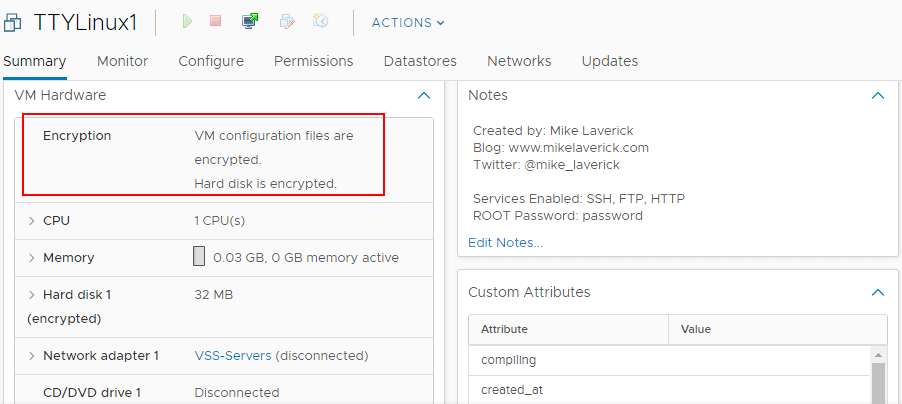
After assigning the VM encryption policy, you will see the Encryption section under the virtual machine properties populated with the status of VM configuration files are encrypted. Hard disk is encrypted.
Concluding Thoughts
Security provided by encryption is the de facto standard in making sure someone does not have unauthorized access to your data. Without the proper decryption mechanisms, the data is simply unreadable to someone without the decryption key. There is no question that VM encryption provides the ultimate level of security for the data found in VM virtual hard disk files. The new functionality contained in VMware vSphere to encrypt the VM configuration and hard disk files provides a powerful way to ensure that virtual machine data is not easily stolen, copied, or access in an unauthorized way outside of the sanctioned VMware vSphere infrastructure. As mentioned, the VM encryption process provides a great way to lockdown sensitive VMs such as domain controllers, sensitive file servers, and other use cases. Using the functionality of the KMS cluster, the VMs are encrypted using the issued keys and the data can be granularly encrypted at the per VMDK level. VMware continues to provide great functionality to ensure the security of virtual infrastructure and protect business-critical and sensitive data.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

