In today’s world, malware and other malicious code is getting more and more sophisticated and leverages new technologies that constantly attempt to circumvent security measures in place. Microsoft has done a good job of continuing to innovate with new technologies designed to make it harder for attackers to steal certain kinds of data that exist inside the operating system. These types of highly valuable pieces of information that exist inside the guest operating system can be security assets such as the authenticated user credentials. Microsoft has introduced a type of technology to help circumvent these types of attacks called Virtualization-based security or VBS. VMware has introduced support for running VBS inside of a virtual machine as of VMware vSphere 6.7.
In this post, we will take a closer look at the virtualization-based security mechanism and how this is implemented in VMware vSphere 6.7 and higher by way of virtual machine configuration.
Table of Contents
- What is Virtualization-based Security or VBS?
- Virtualization-based Security Best Practices
- Enabling Virtualization-Based Security in VMware vSphere
- Enable Virtualization-Based Security on the VMware vSphere virtual machine
- Concluding Thoughts
What is Virtualization-based Security or VBS?
In the introduction, virtualization-based security was introduced as a new technology that helps to protect very sensitive information that is normally found inside Windows operating systems, such as hashed credentials.
How does VBS raise the bar of security to make it more difficult for attackers to obtain this type of information?
Virtualization-based security when implemented in Windows 10 or Windows Server 2016 and higher, uses hardware-assisted virtualization capabilities to create an isolated environment, separate from the operating system, to store sensitive system information.
Microsoft implements this feature in a rather ingenious way by utilizing the Hyper-V hypervisor to host the operating system to create this virtual secure mode which allows enforcing restrictions and protecting system and other operating system resources. Additionally, it is able to protect security information such as authenticated user credentials. When thinking about a system being compromised by malware or other malicious code, when virtualization-based security is being used, the damage that can be inflicted and information that can be stolen by the malware infecting the system can be greatly limited. Even if the malware has control of the OS kernel the underlying Hyper-V hypervisor can protect the sensitive areas of the system from being accessed by the malware.
VBS enables the following security mechanisms to harden your system and isolate key system resources from being compromised:
- Credential Guard – With Credential Guard, VBS can isolate and harden key system and user secrets against compromise
- Device Guard – Helps to prevent malware from being able to run on Windows operating systems
- Configurable Code Integrity
- One mechanism that can be enabled with virtualization-based security is Hypervisor-Enforced Code Integrity (HVCI). Many of the effective security mechanisms that help to filter malicious code allow for enforcing code integrity checks. HVCI uses VBS to check all kernel-mode drivers and binaries before they are started and can prevent unsigned drivers or system files from loading into system memory. Similarly, there is a user-mode variant that enforces checks of applications before they are loaded and will only start those applications that are signed by known, approved signers.
- The Hyper-V hypervisor plays the mediator between applications and memory pages and the permissions that applications have to write across system memory. With these mechanisms in place, malware cannot modify memory and code pages cannot be modified or made executable.
The requirements for implementing Virtualization-based security are the following:
- 64-bit CPU
- Second Level Address Translation or SLAT
- Intel VT-D or AMD-Vi, ARM64 SMMUs
- TPM 2.0
- Firmware support for SMM protection
- UEFI Memory Reporting
- Secure Memory Overwrite Request
- Hypervisor Code Integrity or HVCI compatible drivers
Latest info on Pre-requisites:
To enable Virtualization-Based Security (VBS) on Intel CPUs within your vSphere environment, ensure you are using vSphere 6.7 or a more recent version. Additionally, create a virtual machine configured with hardware version 14 or higher, and choose one of the compatible guest operating systems, such as:
For VBS deployment on AMD CPUs, your vSphere version must be 7.0 Update 2 or newer. Set up a virtual machine with hardware version 19 or higher, and select one of these supported guest operating systems:
Remember to apply the latest patches to your Windows 10, version 1809, and Windows Server 2019 installations before enabling VBS.
For additional guidance on enabling VBS on virtual machines using AMD platforms, refer to the VMware Knowledge Base article available here: https://kb.vmware.com/s/article/89880.
Virtualization-based Security Best Practices
What are some best practices when it comes to implementing Windows Virtualization-based security in the context of VMware virtual machines?
The following considerations need to be made.
- VBS Hardware – You need the following Intel hardware for VBS
- Haswell CPU or later
- Not all VBS functionality is available on AMD CPUs
- Windows Guest OS Compatibility – The following operating systems are supported in the context of VBS running inside of vSphere 6.7:
- Windows 10 and Server 2016
- Unsupported VMware Features with Virtual Machines that have VBS enabled
- Fault tolerance
- PCI passthrough
- Hot add of CPU or memory
- Installation and Upgrade considerations:
- If Virtual machine versions less than VM version 14 are used with Windows 10 and Windows Server 2016, you must reinstall the operating system if you change to UEFI from BIOS.
- If migrating virtual machines from previous vSphere releases to vSphere 6.7 and higher and plan on enabling VBS in the future, use UEFI to avoid an OS reinstall after the upgrade.
Enabling Virtualization-Based Security in VMware vSphere
The new virtualization-based security feature that is found in VMware vSphere 6.7 and higher can be enabled at the virtual machine level inside the vSphere client. In fact, you have to enable the feature at the virtual machine level first, and then enable the feature inside of the Windows operating system.
Enable Virtualization-Based Security on the VMware vSphere virtual machine:
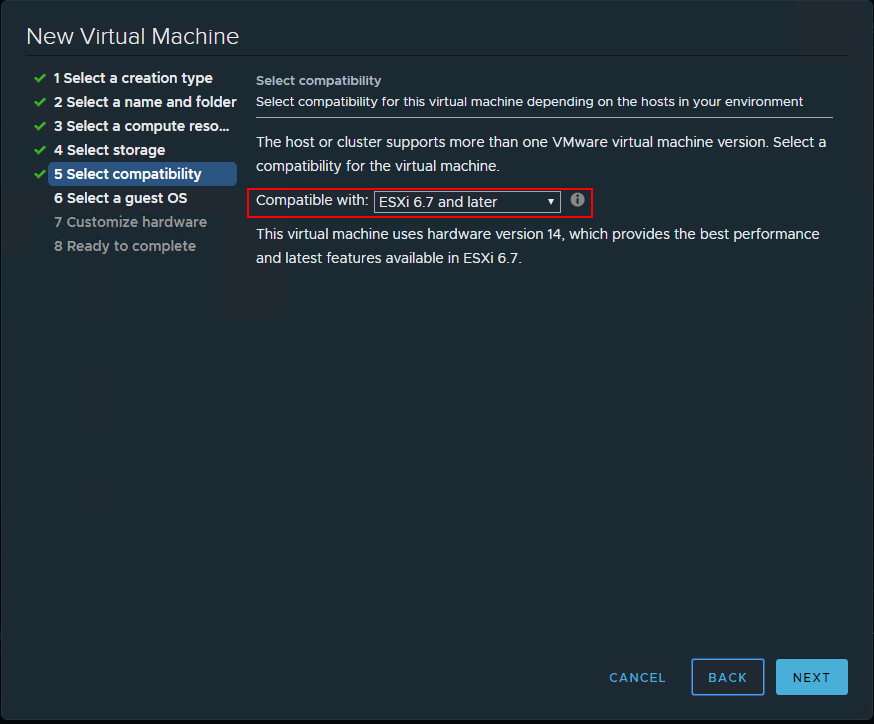
When you create a new virtual machine, the step, Select Compatibility needs to be configured for ESXi 6.7 and later to be able to configure the virtualization-based security mechanism.
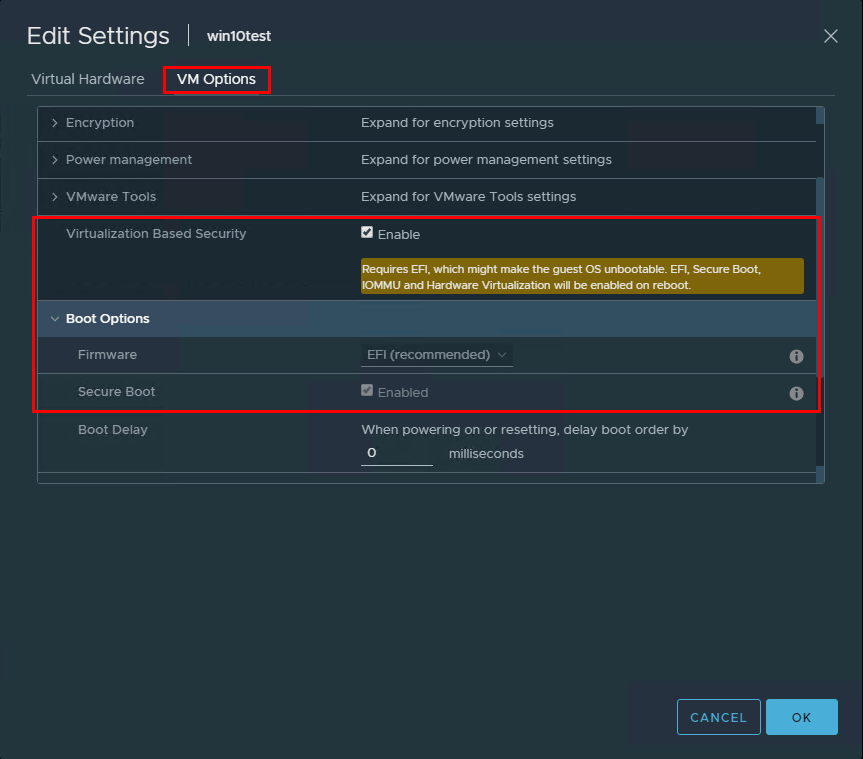
Once you have created a new virtual machine, go into the properties of the virtual machine and click the VM Options tab. Look for the Virtualization Based Security section. Place a checkbox in the Enable field. Also, make sure the Secure Boot is enabled and UEFI.
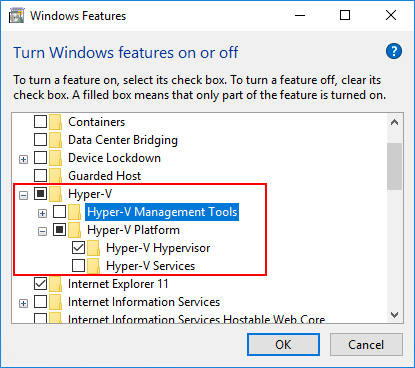
Now, it is simply a matter of installing the Hyper-V feature and configuring VBS.
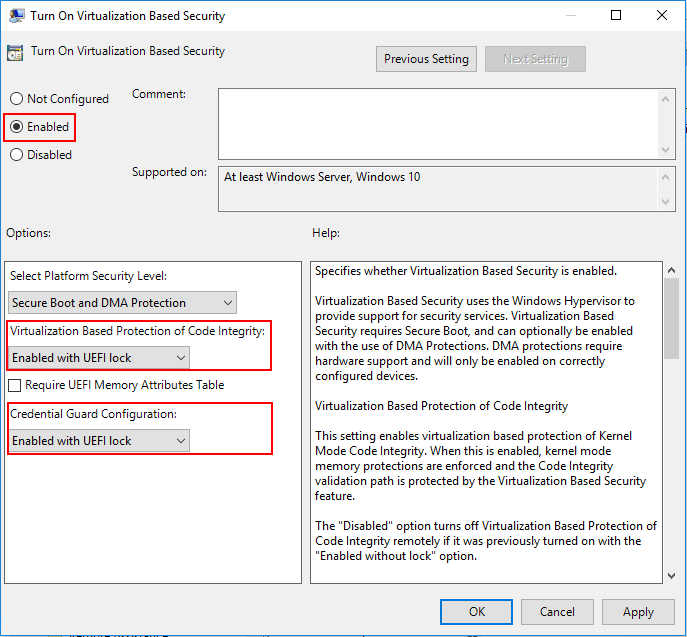
Navigate to Computer Configuration >> Administrative Templates >> System > Device Guard >> Turn On Virtualization Based Security
Concluding Thoughts
Windows Virtualization-based Security is a great new feature found in the latest Windows operating systems, including Windows 10 and Windows Server 2016. The VBS feature allows Windows to have further protection against malware and other malicious code that may attempt to steal credentials or other sensitive system information. It does this by using the Hyper-V hypervisor to provide the protected memory space needed so these types of sensitive data can be protected separately and isolated from the guest operating system.
VMware allows using VBS as of vSphere 6.7. The configuration is made at the VM level first to turn on the capability and then enabled within the Windows operating system by flagging on the Hyper-V feature and then enabling VBS using the policy setting.
In today’s security vulnerable and sensitive world, organizations must use the latest capabilities and security features to stay ahead of attackers and malicious code attempting to circumvent more traditional security. Be sure to check out virtualization-based security in both Windows and VMware vSphere 6.7 and higher.
Ensure the safety of your important data with a reliable VMware backup solution that acts as a strong shield. Explore its capabilities without any financial commitment.
Easily strengthen your VMware environment and gain peace of mind by downloading BDRSuite today.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

