What is AWS Firewall Manager?
AWS Firewall Manager is a security management service that allows you to configure and manage firewall rules applied on all AWS resources spread across on all your AWS accounts and applications hosted on AWS Cloud under various geographical locations.
If you want to protect your entire AWS Organization infrastructure instead of a selective number of accounts/resources, or if you want to add new resources to be protected, AWS Firewall Manager allows you to secure your resources with centralized monitoring of DDoS attacks across all accounts/resources in your AWS Organization.
Prerequisites for setting up AWS Firewall Manager
- Your AWS account must be in an organization in AWS Organization, and the organization must have all features enabled
- Only the AWS account set as AWS Firewall Manager administrator account can configure security policies. The master account in your AWS Organization can designate this account as a Firewall Manager administrator account.
- You must enable AWS Config for each member account in your organization in AWS Organizations and for each AWS Region that contains the resources that you want to protect using AWS Firewall Manager security policies.
If you login to a non-administrator account or not a part of AWS Organization, and want to use the AWS Firewall service, you will get an alert as below.
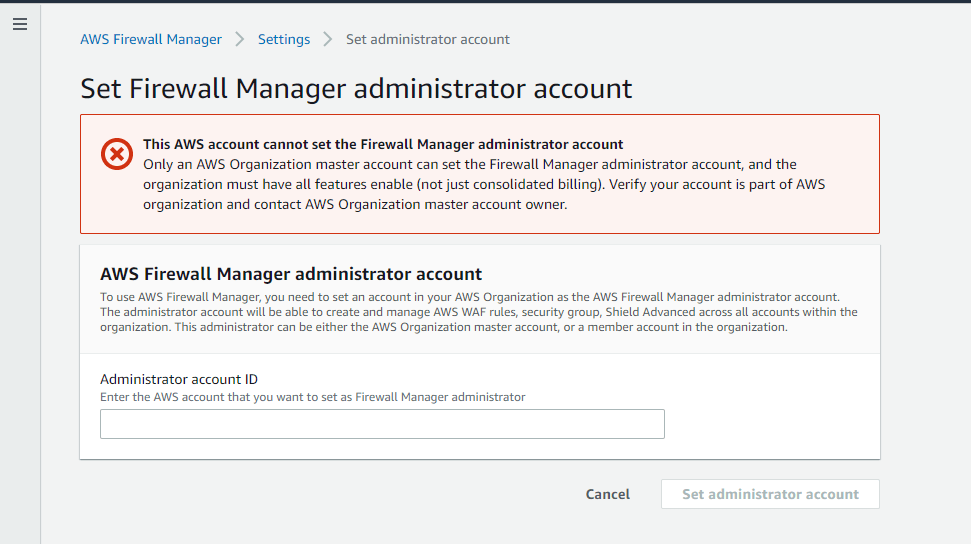
And provide your Administrator account ID to set your current account as Firewall Manager administrator.
What is AWS WAF (Web Application Firewall)?
AWS WAF is a web application firewall that lets you monitor the HTTP and HTTPS requests that are forwarded to an Amazon API Gateway API, Amazon CloudFront, or an Application Load Balancer. Along with AWS Firewall Manager & AWS WAF, you can create a new ACL or use the predefined ACL.
Creating Web ACL
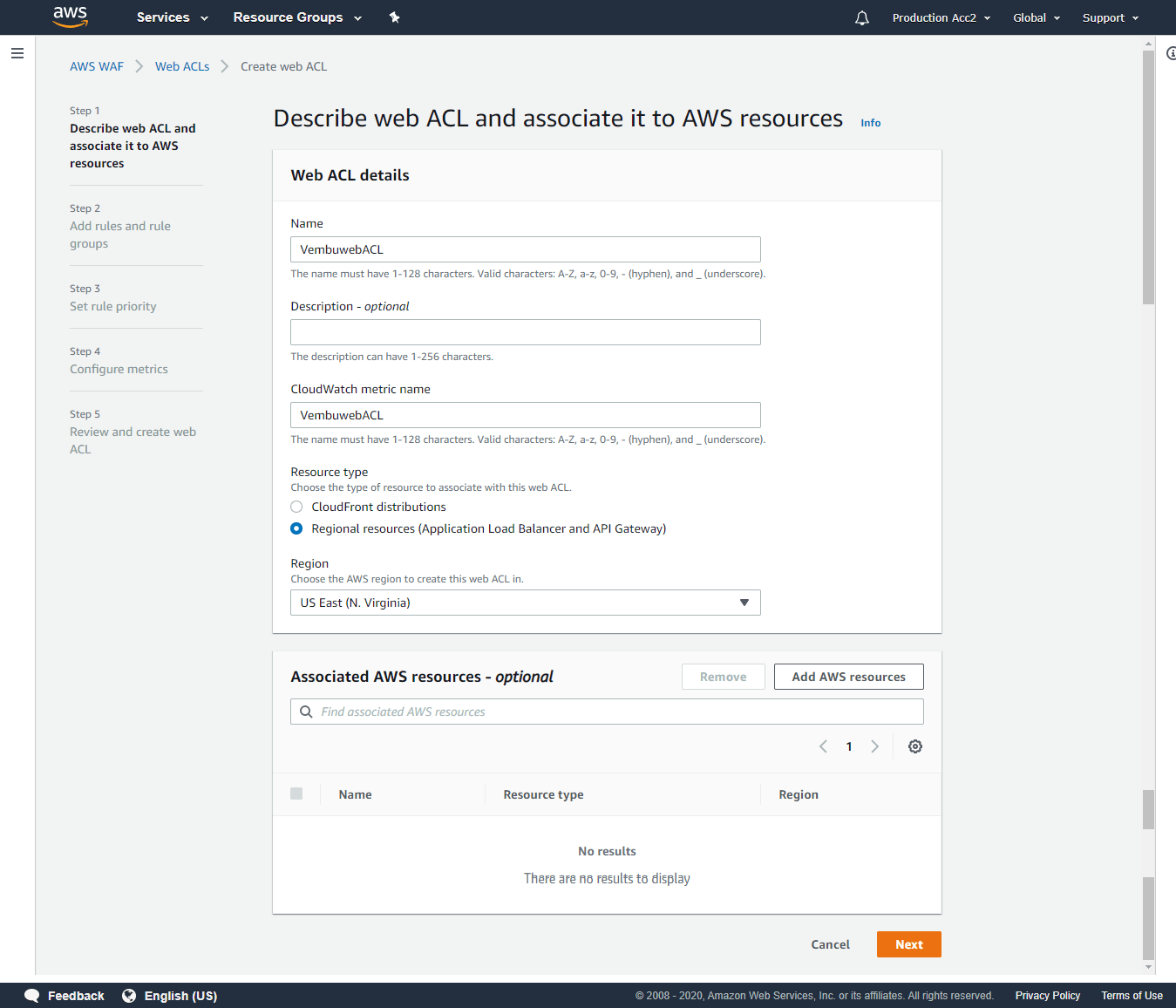
Step 1: Describe Web ACL and associate it to AWS resources
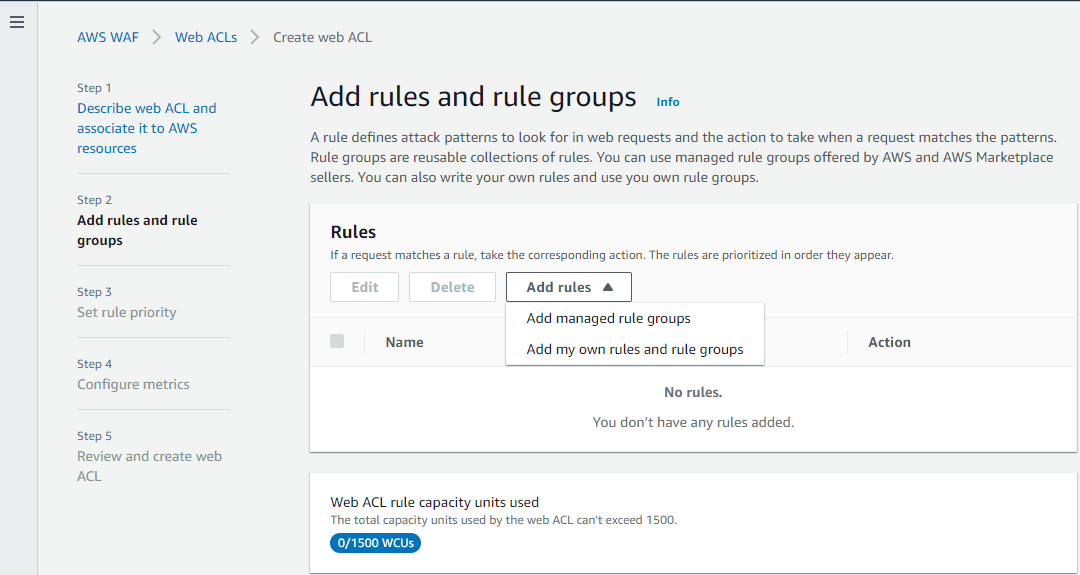
Step 2: Add rules and rule groups
A rule defines attack patterns to look for in web requests and the action to take when a request matches the patterns. Rule groups are reusable collections of rules. You can use managed rule groups offered by AWS and AWS Marketplace sellers. You can also write your own rules and use your own rule groups.
While creating you can conveniently select managed rule groups or your own rule groups. Based on the selection, your create wizard will change.
Managed rule groups
Managed rule groups are created and maintained for you by AWS and AWS Marketplace sellers. Some of these managed rule groups are given below with descriptions. You just need to enable any of these rules to add to your Web ACL.
- Admin protection – Contains rules that allow you to block external access to exposed admin pages through third-party software.
- Amazon IP reputation list – Contains rules that are developed from Amazon threat intelligence. This is useful to block sources associated with bots or other threats.
- Anonymous IP list – Contains rules that allow you to block requests from services that hide viewer identity. This can include requests originating from VPN, proxies, Tor nodes, and hosting providers. This is useful to filter out viewers trying to hide their identity from your application.
- PHP application – Contains rules that block request patterns associated with exploiting vulnerabilities specific to the use of the PHP, including injection of unsafe PHP functions. This can help prevent exploits that allow an attacker to remotely execute code or commands
- WordPress application – Contains rules that block request patterns associated with the exploitation of vulnerabilities specific to WordPress sites. Other than AWS, there are third party managed rule groups also available to select.
In our case, we are selecting our own rules and rule groups.
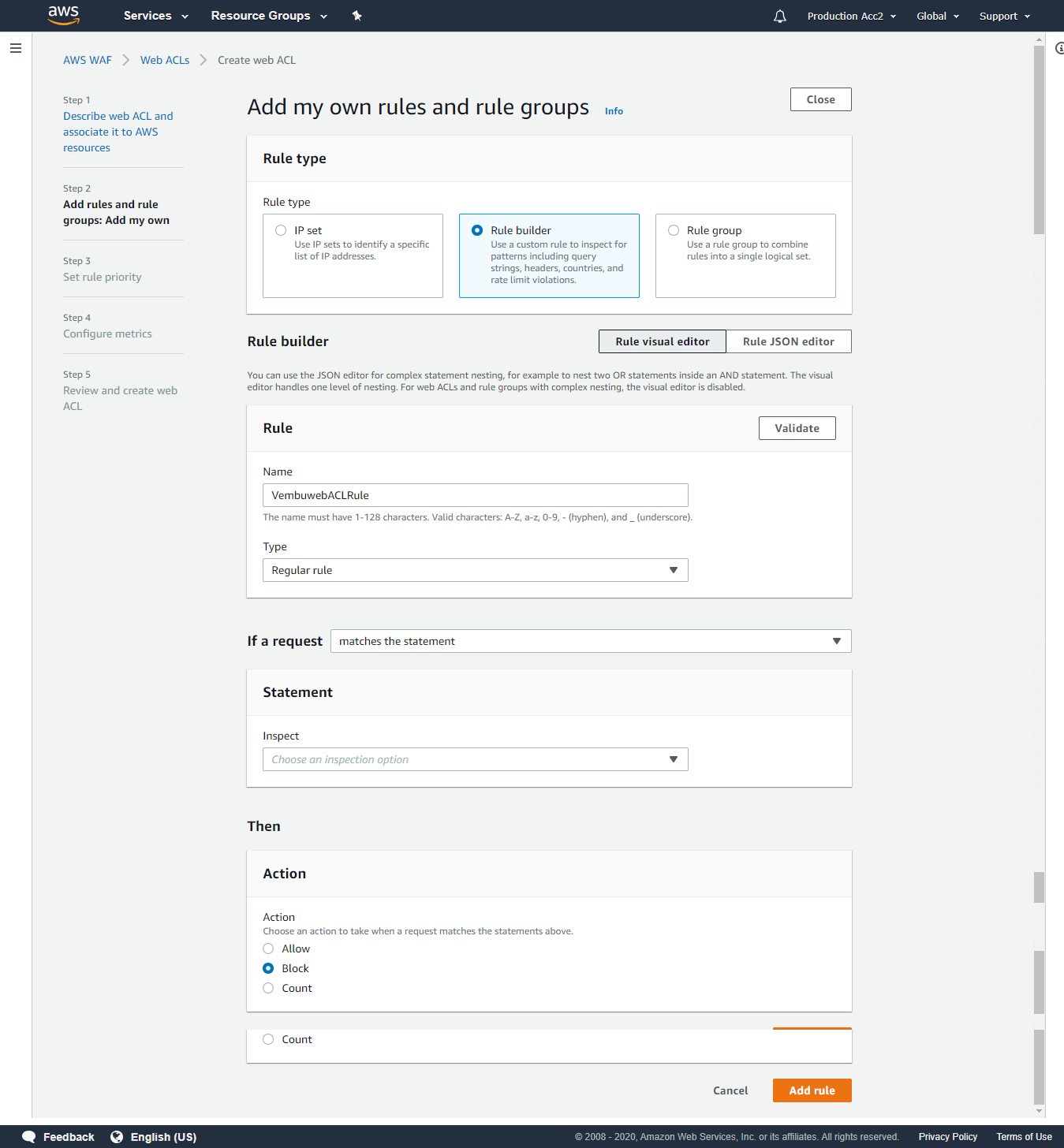
Add my own rules and rule groups
Rule type:
IP Set – Use IP sets to identify a specific list of IP addresses
Rule builder – Use a custom rule to inspect for patterns including query strings, headers, countries, and rate limit violations.
Rule Group – Use a rule group to combine rules into a single logical set.
You can choose any of these three types to continue based on your requirement. We are choosing Rule builder.
After selecting the rule type, provide a Name for the rule.
Next, select Type – Regular rule or Rate-based rule. Rate–based rules are identical to regular rules, but also take into account how many requests arrive from an IP address in a five-minute period. We are selecting Regular rule.
Next choose, if a request matches any one of the below statements as per your firewall rule that you are creating.
- Matches all the statements (AND)
- Matches at least one of the statements (OR)
- Does not match the statement (NOT)
Inspect – In this section where to check the matching condition and the matching components to apply the rule
- Originate from the Country in – You need to provide the country code from the available list
- Originate from the IP Address in – You need to provide the IP set
Available matching components to inspect
- Header – Based on Header field name, match type and text transformation
- Single query parameter – Based on query argument match type
- URI path – URI path match type
- Query string – String match type
- Body – Body match type
- HTTP method – Select the action when a request matches the statements above and click Add rule.
- Allow
- Block
- Count
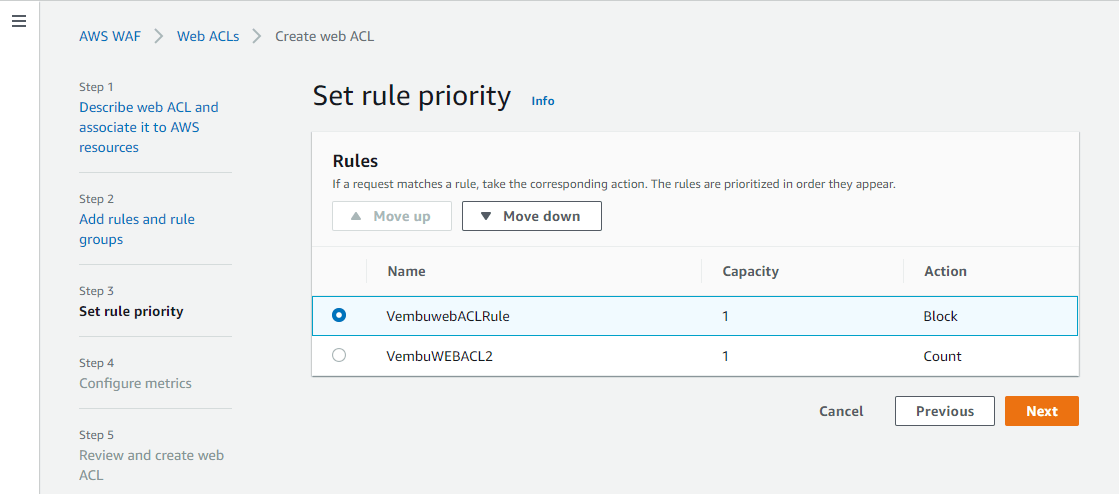
Step 3: Set rule priority
AWS WAF evaluates the rules and rule groups in the order shown, starting from the top. Move rules up or down to change the evaluation order. The order of evaluation affects the behavior of the Web ACL. AWS WAF scans the rule from top to bottom, so a Deny Rule at the bottom of the rule will affect the same allow rule on top of the list. You can move UP and Down when selecting the required rule name by pressing the Move up and Move down button.
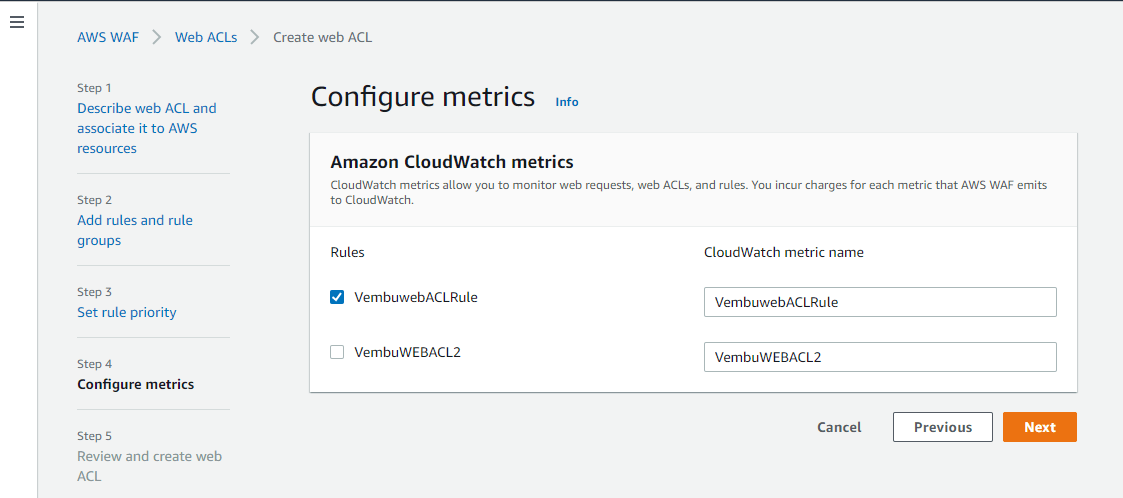
Step 4: Configure Metrics
You can use Amazon CloudWatch metrics to monitor and troubleshoot your AWS WAF resources. Choose the rules and rule groups that you want to emit metrics to CloudWatch. You can publish metrics for multiple rules to a single CloudWatch metric by specifying the same metric name for multiple rules. Click Next to continue.
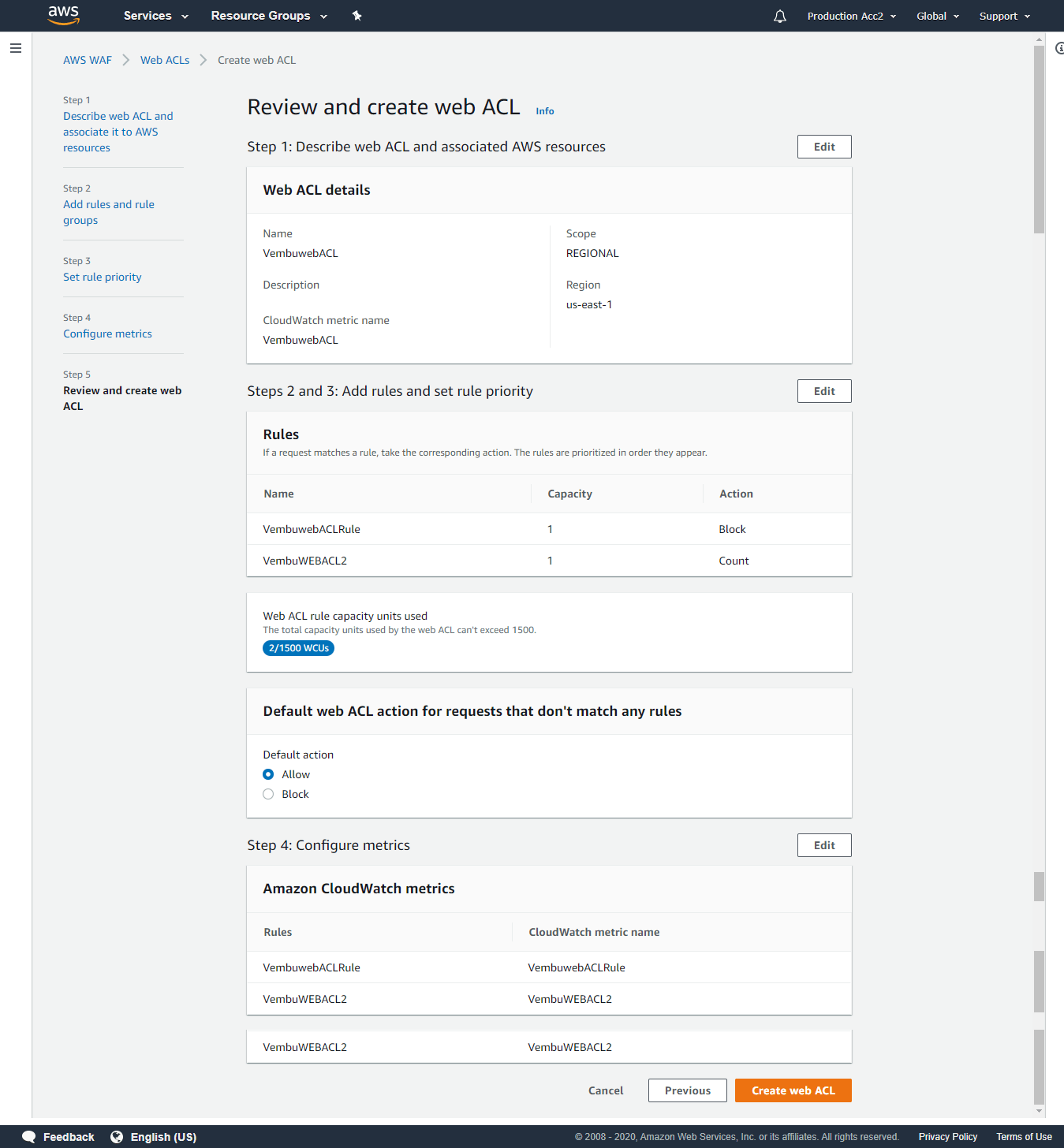
Step 5: Review and create Web ACL
On this final step, Check your web ACL settings, make any changes you need, then choose Create to create the web ACL.
Deleting a Web ACL
If you want to delete a rule, you need to first remove the rule from the Web ACLs that are using it and remove the conditions that are included in the rule.
- Sign in to the AWS Management Console and open the AWS WAF console at https://console.aws.amazon.com/wafv2/
- To remove the rule from the web ACLs that are using it, perform the following steps:
- In the navigation pane, choose Web ACLs.
- Choose the name of a web ACL that is using the rule that you want to delete.
- Choose Edit web ACL.
- Choose the X to the right of the rule that you want to remove from the web ACL, and then choose Update.
- Repeat for all of the remaining web ACLs that are using the rule that you want to delete.
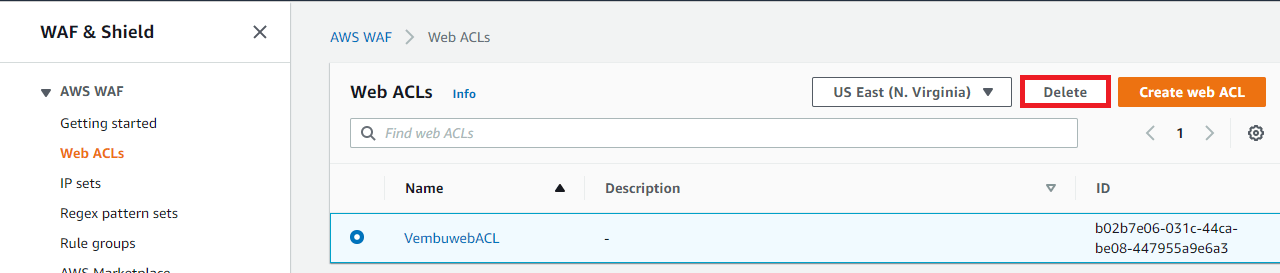
- In the navigation pane, choose Rules.
- Select the name of the rule you want to delete.
- Choose Delete.
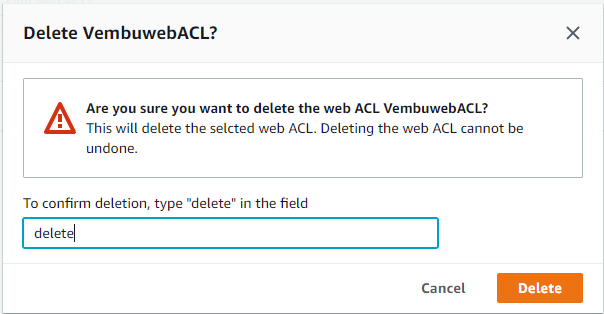
To conform deletion, type delete in the provided box and click Delete button.
IP Set
An IP set is a collection of IP addresses and IP address ranges that you use in a rule statement. To use an IP set in a web ACL or rule group, you first create an IP set with your IP address specifications. Then you reference the set when you add the IP set rule statement to a web ACL or rule group.
During Web ACL creation, if you choose to use the IP Set based rule, you need to create an IP Set to use in your rule group. When you choose Rule builder while creating your own rule and rule groups, you have the option to choose the statement that matches where you want to choose the option Originates from an IP address. In this case, creating an IP Set is a must before creating web ACL
Create IP Set
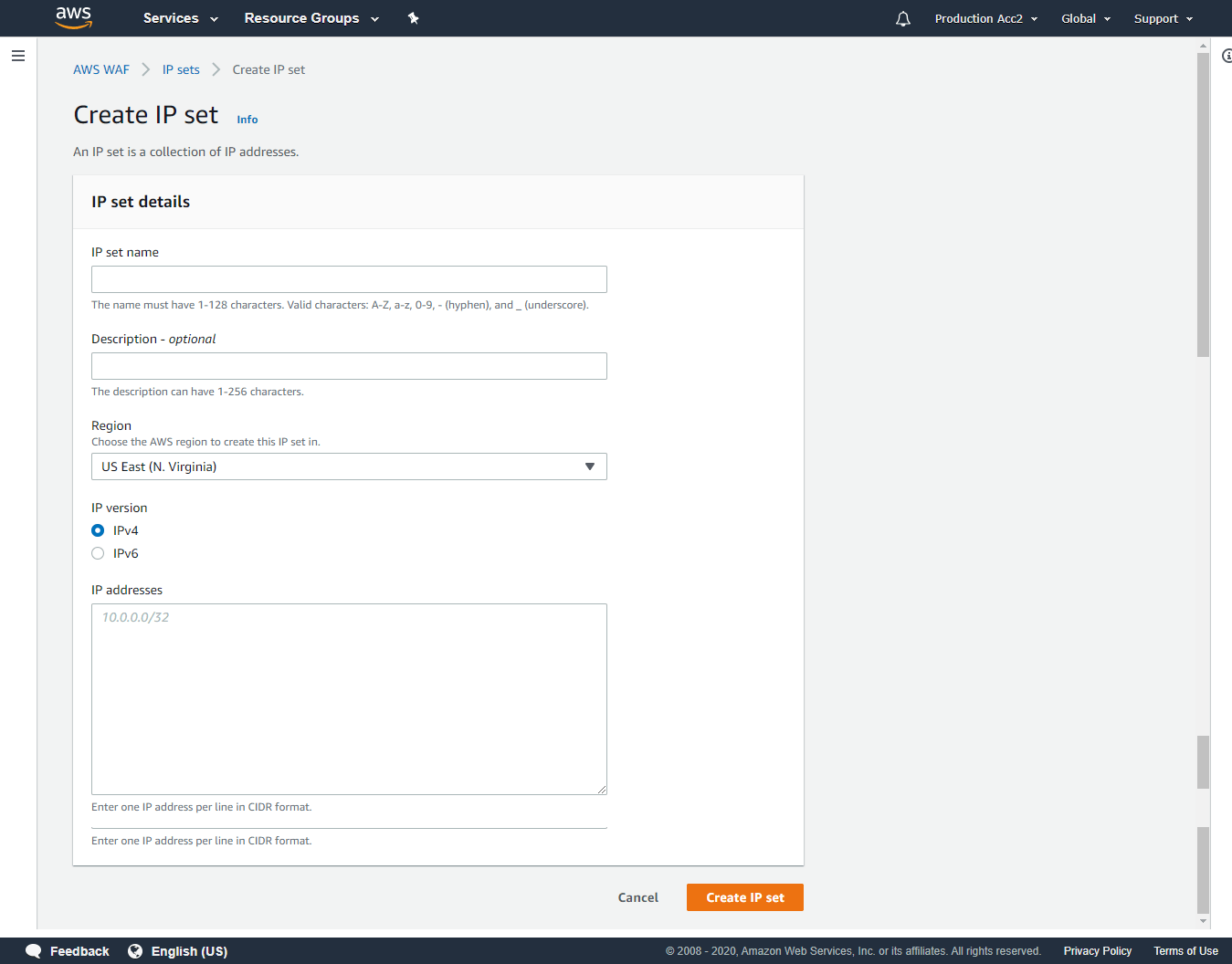
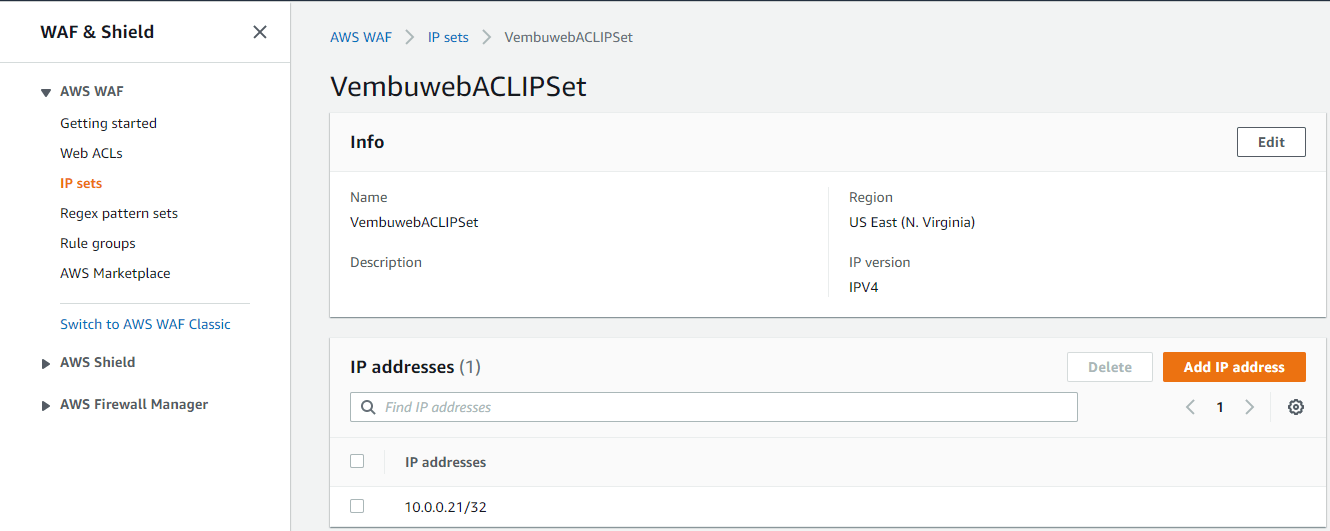
Provide an IP set name, choose the region where you want to deploy the Web ACL rule to use this IP Set, select IP version and provide the IP details in CIDR format. Then click Create IP set. Once created, you will get all the details of the IP set as below
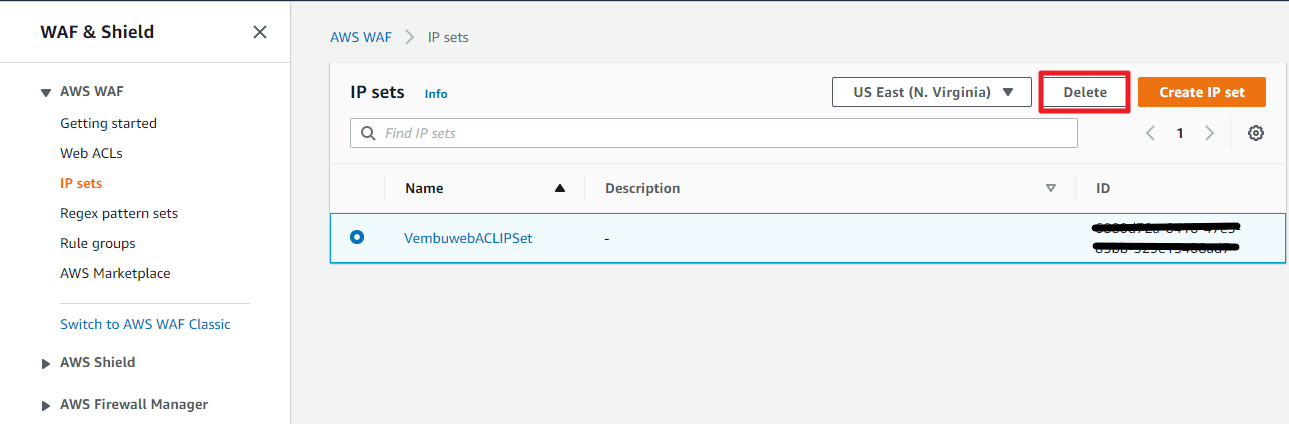
Deleting an IP set
Before deleting the Web ACL rule, delete the associated IP set first. For deleting the IP set, select the particular IP set created, and choose the Delete button. On confirmation the IP set will be deleted.
Conclusion
AWS Web application firewall is very effective in preventing attacks aimed at the web application level. Combined with other AWS security solutions like AWS Shield & AWS Firewall Manager, you can safeguard your total AWS Infrastructure along with the web applications from cyber attacks.
Start free trial of Vembu Backup for AWS
Vembu BDR Suite offers an agentless and cloud-native backup solution to protect your instances across any AWS account and region while ensuring instant recovery options.
- Backup from any AWS account and region
- Flexible Backup scheduling and retention
- Application-aware processing
- Instance-level and Volume-level Recovery
To learn more about Vembu Backup for AWS, click here.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

