Table of Contents
- Introduction
- What is Azure Active Directory?
- Premium features available in Azure AD Premium P1 and P2
- What is available in Premium P2 and not in Premium P1?
- Identity Protection
- Identity Governance
- Identity Protection
- User risk policy
- Sign-in risk policy
- MFA registration policy
- Risky users report
- Risky sign-in report
- Risk detections report
- Privileged Identity Management (PIM)
- Conclusion
Introduction
What is Azure Active Directory?
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service, which helps an organization and its employees sign in and access resources.
The resources can be external resources like Microsoft 365, Azure portal, and over 100 third-party SaaS applications, or internal resources such as apps on an organization’s corporate network and intranet, along with any cloud apps developed by any organization for its internal purposes. Many big organizations use Azure AD as an extension of their OnPremise Windows AD to use their resources internally and externally with the same identity.
Microsoft Online business services, such as Microsoft 365 or Microsoft Azure, require Azure AD for sign-in and to help with identity protection. If you subscribe/purchase to any Microsoft Online business service, the subscriber automatically gets Azure AD with access to all the free features.
To enhance the existing Azure AD implementation, the subscriber can also add paid capabilities by upgrading the existing Free Azure AD to Azure Active Directory Premium P1 or Premium P2 licenses. Azure AD paid licenses are built on top of the existing free directory, providing self-service, enhanced monitoring, security reporting, and secure access for mobile users.
In this blog, we are providing an overview of some of the additional features that cover Azure AD Premium P1 and Premium P2 licenses. Administrators can purchase these licenses on a subscription basis after evaluation of the features too. Microsoft provides a free trial for a monthly subscription for evaluation.
Access URL: https://aad.portal.azure.com/
Log in to the Azure AD portal → On “My Dashboard,” click “Try Azure AD Premium” -> Click “Activate under Free Trial,” on Azure AD Premium P2. You can see a notification “Successfully activated Azure AD Premium P2 trial”.
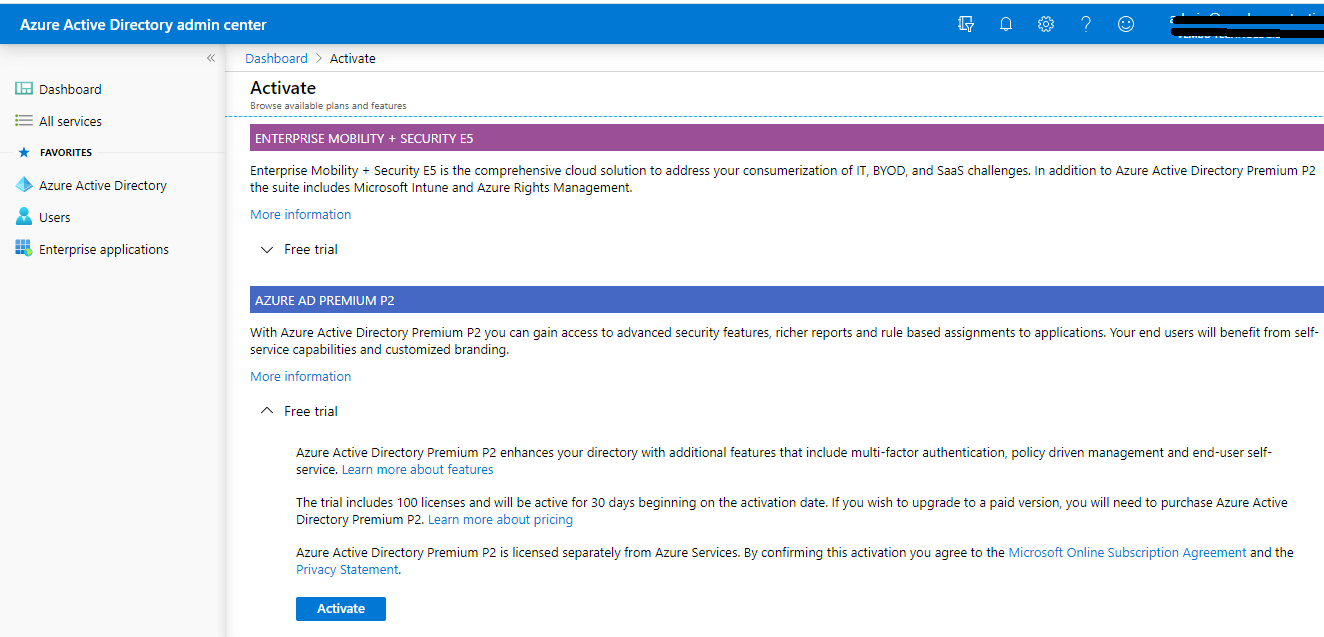
Premium features available in Azure AD Premium P1 and P2
Password Protection (custom banned passwords), Password Protection for Windows Server Active Directory (global and custom banned passwords), Self-service password reset/change/unlock with on-premises write-back, Group access management, Microsoft Cloud App Discovery, Microsoft Azure AD Join: MDM auto-enrollment and local admin policy customization, Microsoft Azure AD Join: self-service BitLocker recovery, enterprise state roaming, advanced security, and usage reports.
Hybrid Identities
Application Proxy, Microsoft Identity Manager user CAL, Connect Health
Advanced Group Access Management
Dynamic groups, Group creation permission delegation, Group naming policy, Group expiration, Usage guidelines, Default classification.
Conditional Access
Conditional Access based on the group, location, and device status, Azure Information Protection integration, SharePoint limited access, Multi-Factor Authentication with Conditional Access, Microsoft Cloud App Security integration, and 3rd party identity governance partner integration.
All these above features are commonly available on Azure Free Office 365, Premium1, and Premium2 subscriptions.
What is available in Premium P2 and not in Premium P1?
The below features Identity Protection and Identity Governance are exclusive features for Premium P2. In this blog, we are detailing these two main features of Azure Premium P2 Identity Protection and Privileged Identity Management (PIM) in Identity Governance
Identity Protection
Vulnerabilities and risky accounts detection, Risk events investigation, and Risk-based Conditional Access policies
Identity Governance
Privileged Identity Management (PIM), Access Reviews, and Entitlement Management.
Identity Protection
Identity Protection is a tool that allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks
- Investigate risks using data in the portal
- Export risk detection data to third-party utilities for further analysis
Administrators can review detections and take manual action on them if needed. There are three key reports that administrators use for investigations in Identity Protection:
- Risky users
- Risky sign-ins
- Risk detections
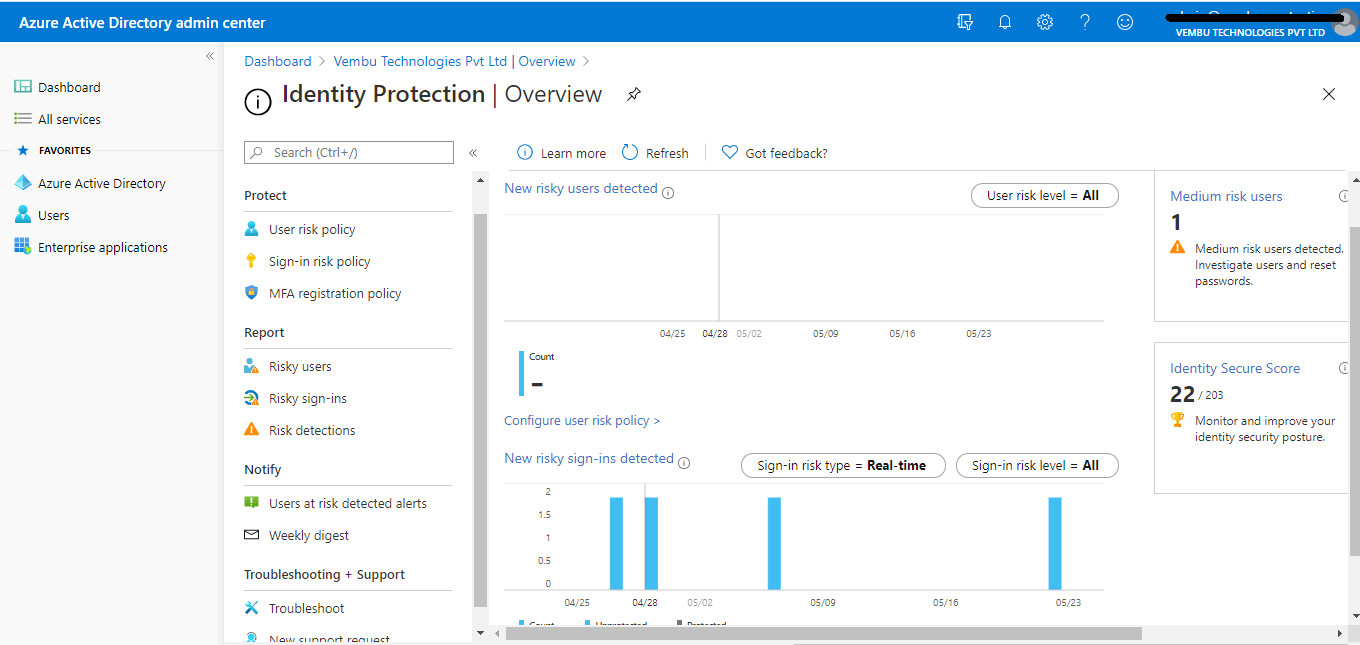
The identity Protection menu blade has four main parts viz Protect, Report, Notify, and Troubleshooting + Support
Protect – User risk policy, Sign-in risk policy, and MFA registration policy
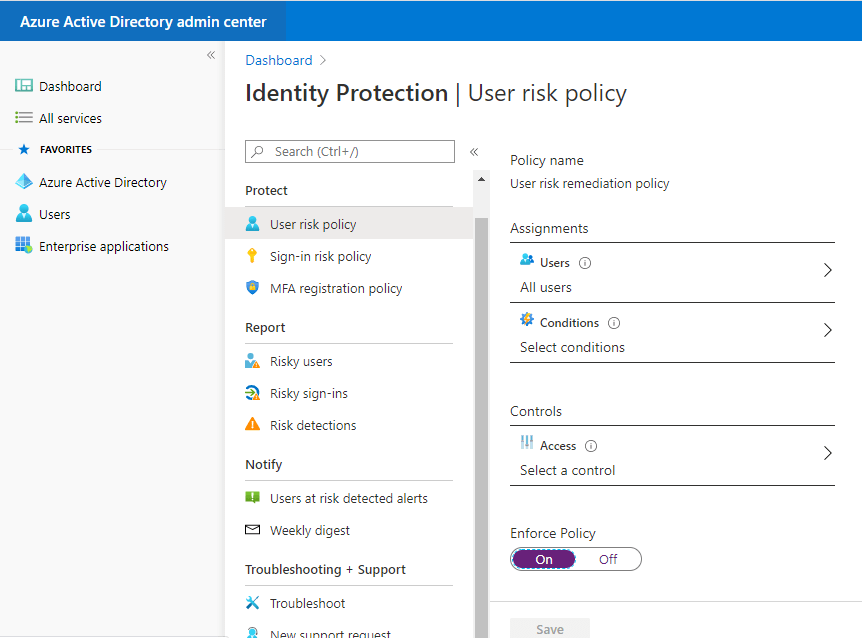
User risk policy
Here, administrators can enable a user risk policy to protect users and can remediate based on all users/individual and group members (they can exclude any members ). Administrators can set the conditions when the risk policy should apply based on the user’s risk level ( Low, Medium, and High). The end result will be to either block access or allow access to enable multi-factor authentication requirements.
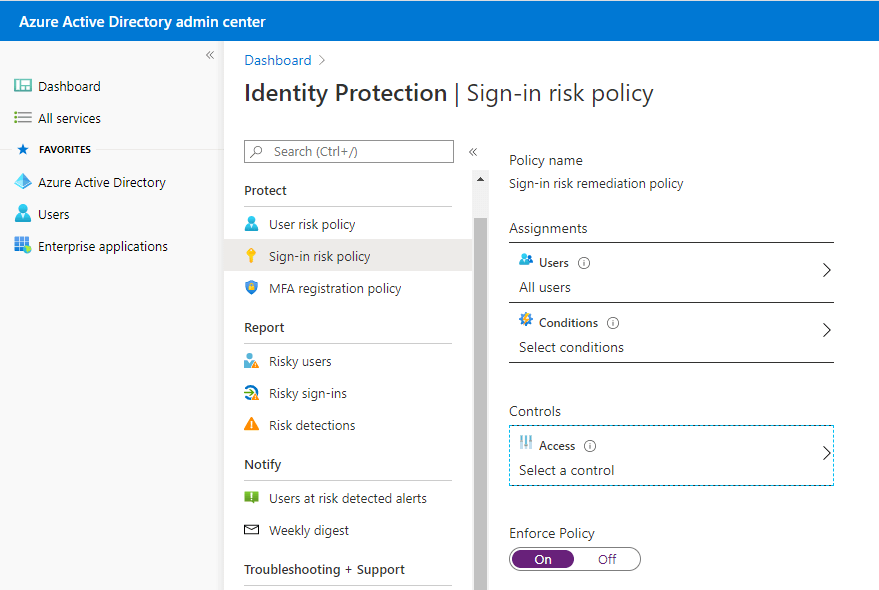
Sign-in risk policy
Here, administrators can enable a sign-in risk policy to protect sign-in users and can remediate based on all users/individual and group members ( can exclude any members ). Administrators can set the conditions when the risk policy should apply based on the user’s risk level ( Low, Medium, and High). The end result will be blocked access or allowed access with password rechange requirements.
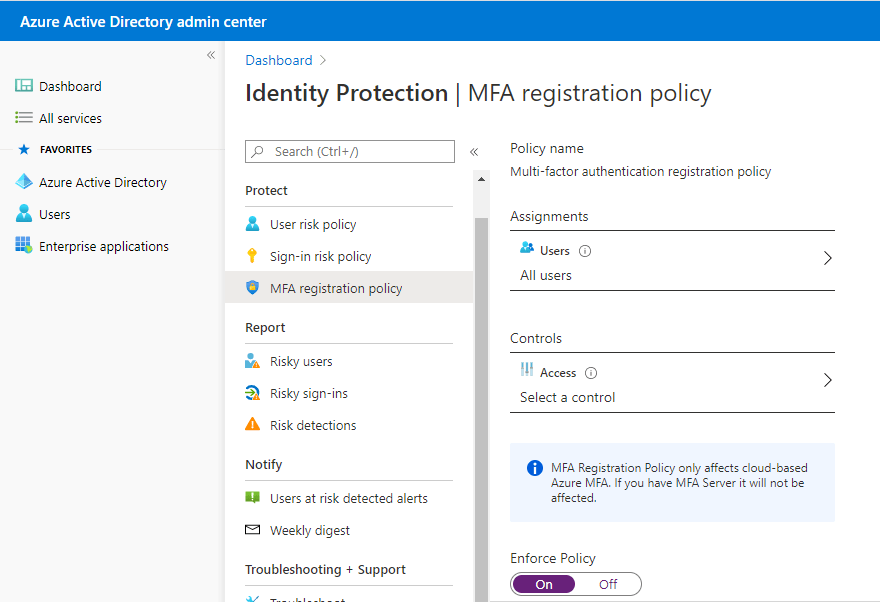
MFA registration policy
Azure Multi-Factor Authentication provides a means to verify every user who is using more than just a username and password. It provides a second layer of security to user sign-ins. In order for users to be able to respond to MFA prompts, they must first register for Azure Multi-Factor Authentication. This registration policy only supports Azure MFA and not OnPremise MFA servers or third-party MFA apps. Here too, administrators can enforce it for all users/individuals or just a group member based on Azure MFA registration enforcement.
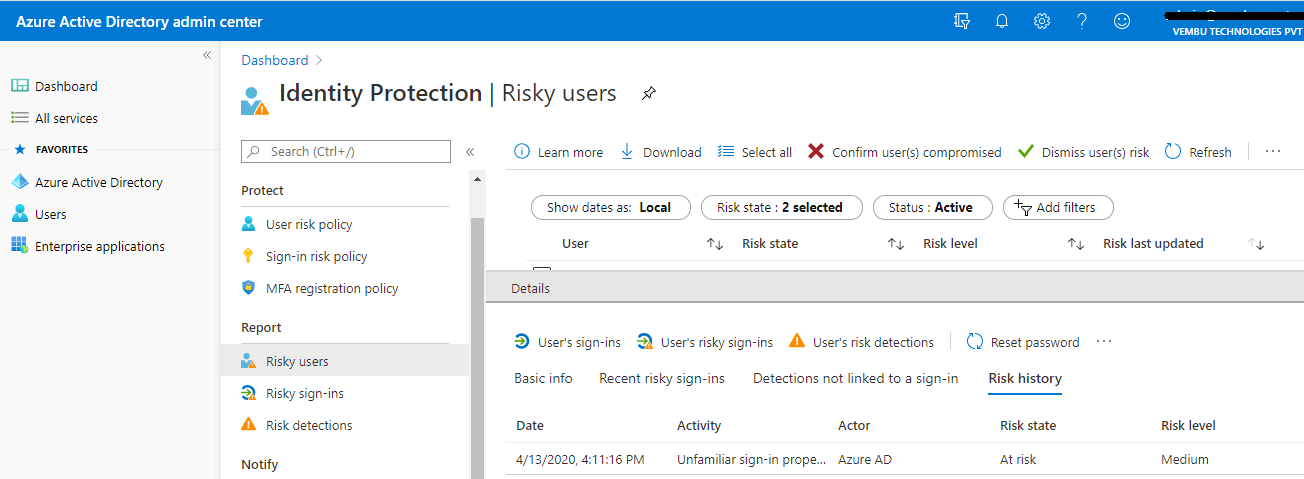
Risky users report
This report section shows users flagged for risk due to risky sign-in, an indicator for a sign-in attempt that might have been performed by someone who is not the legitimate owner of a user account; and Users flagged for risk – A risky user is an indicator of a user account that might have been compromised.
In this report, by selecting each user listed, we can get detailed information such as basic information about the user, his recent risky sign-in, detections not linked to a sign-in, and his past risk history.
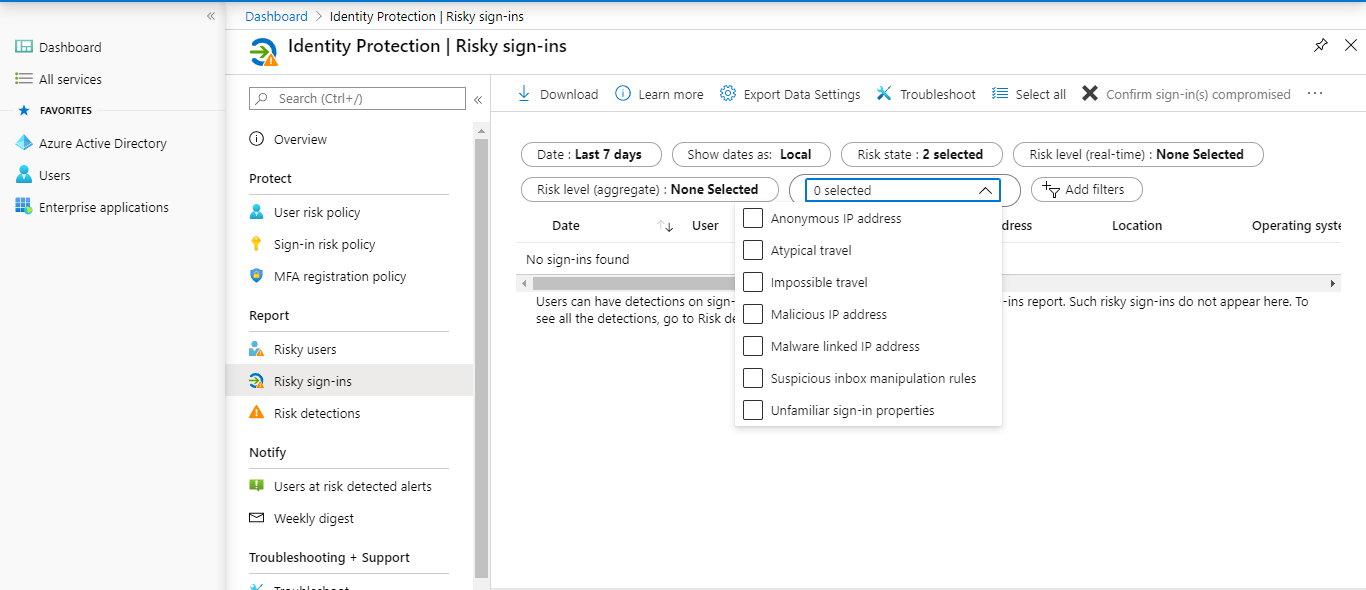
Risky sign-in report
A comprehensive risky sign-in activity on any users. Administrators can filter based on
Date – Last 1 month, last 7 days, last 24 hours, and custom time interval
Risk state – At risk, confirmed compromised, confirmed safe, dismissed, and remediated
Risk level – High, Medium, and Low
Detection type – Anonymous IP address, Atypical travel, Impossible travel, Malicious IP address, Malware linked IP address, Suspicious inbox manipulation rule, and Unfamiliar sign-in properties.
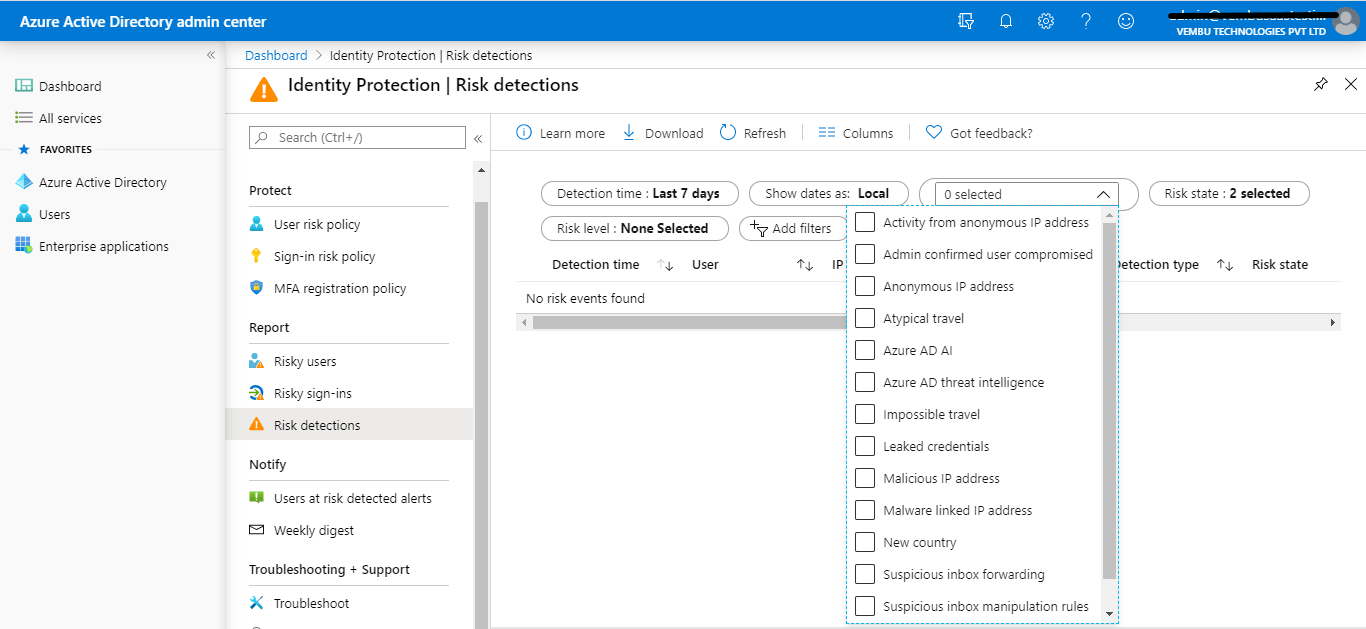
Risk detections report
The risk detections report contains filterable data for up to the past 90 days (3 months).
With the information provided by the risk detections report, administrators can find:
- Information about each risk detection including type
- Other risks triggered at the same time
- Sign-in attempt location
- Link out to more detail from Microsoft Cloud App Security (MCAS)
Administrators can then choose to return to the user’s risk or sign-ins report to take actions based on the information gathered.
Privileged Identity Management (PIM)
Azure Active Directory (Azure AD) Privileged Identity Management (PIM) is a service that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services like Office 365 or Microsoft Intune. Azure AD PIM is a premium feature that enables Global administrators to limit standing admin access to privileged roles and much more. This evolves in Four steps
Assign
Assign users or current admins as eligible admins for specific Azure AD roles, so that they only have access when necessary
Activate
Activate your eligible admin roles so that you can get limited standing access to the privileged identity
Approve
View and approve all activation requests for specific Azure AD roles that you are configured to approve
Audit
View and export the history of all privileged identity assignments and activations so you can identify attacks and stay compliant
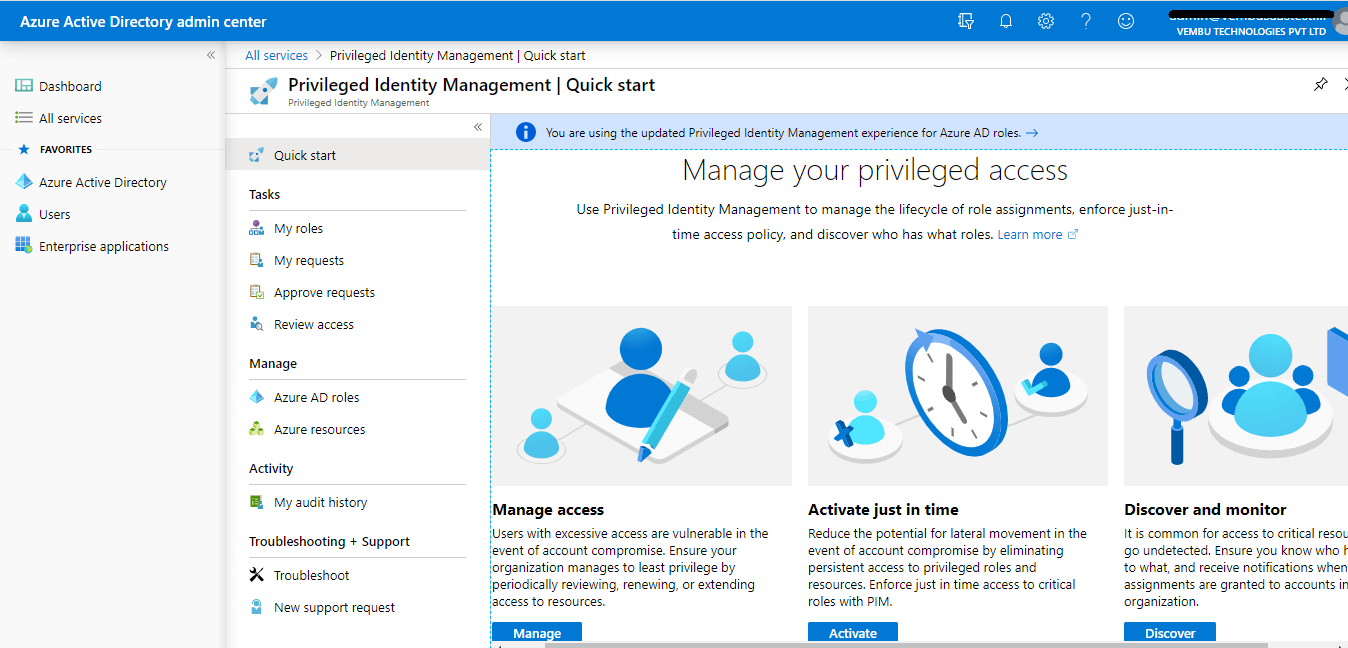
Manage access
Assigning roles to users is a pretty straightforward one. Users with excessive access i.e. assigning a particular user to various administrative roles are vulnerable in the event of account compromise. A Global administrator should review, renew and extend access to resources periodically
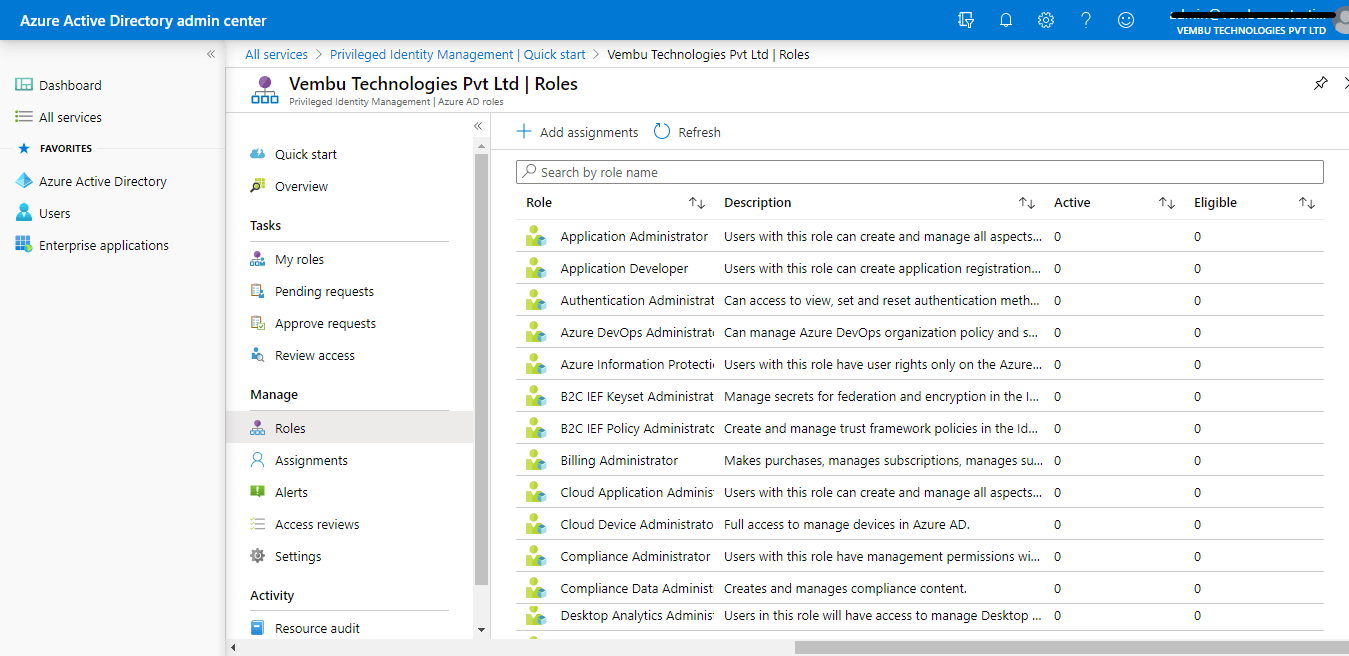
Activate just in time
Also, it’s good practice to assign important roles such as Exchange administrators to users for a period of time. At any time, a Global administrator can review and extend his role when needed.
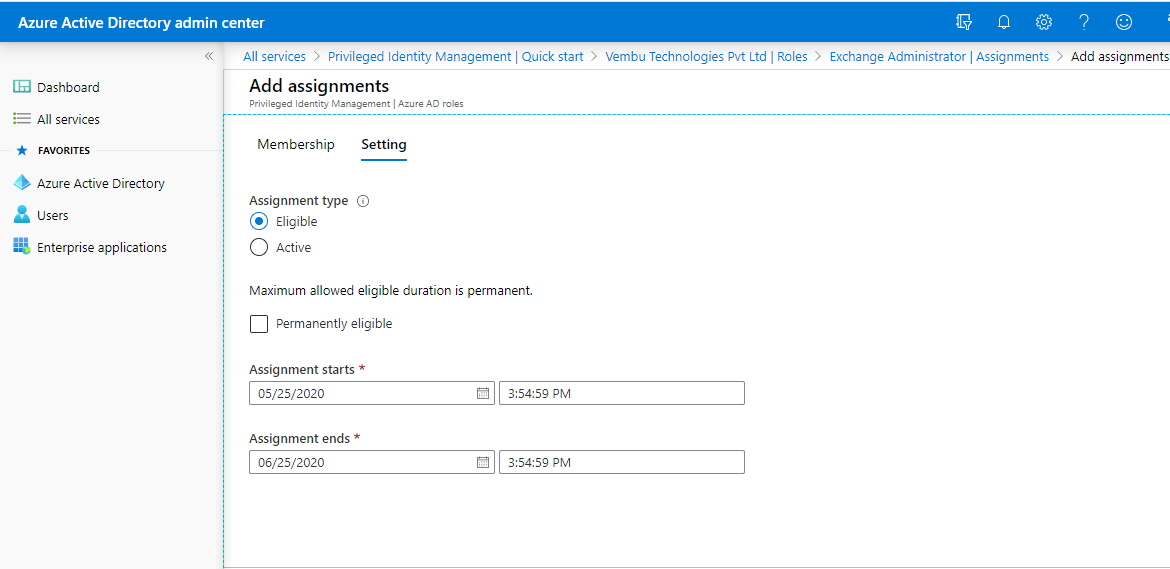
A Global administrator can choose the assignment type as either eligible or active. He can revoke permanently eligible options and provide a duration for a user’s role.
Discover and Monitor
Select the assigned user & view their role assignment for continuous monitoring. Ensure the Administrator should know who has access to what, and receive notifications when new assignments are granted to accounts in an organization. Select the member and check his roles, under Eligible role, Active role, and Expired role. Monitor the user periodically
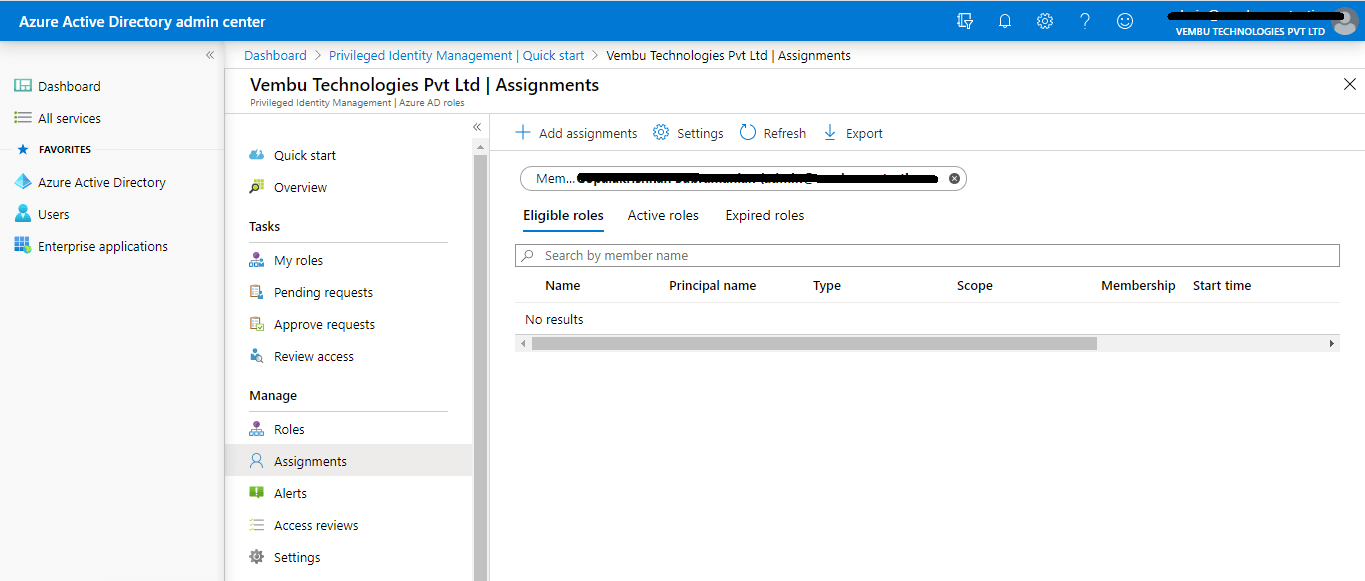
For example, a user assigned with an Exchange administrator role checks his Exchange administrator role settings and monitors his role change through send mail notifications settings.
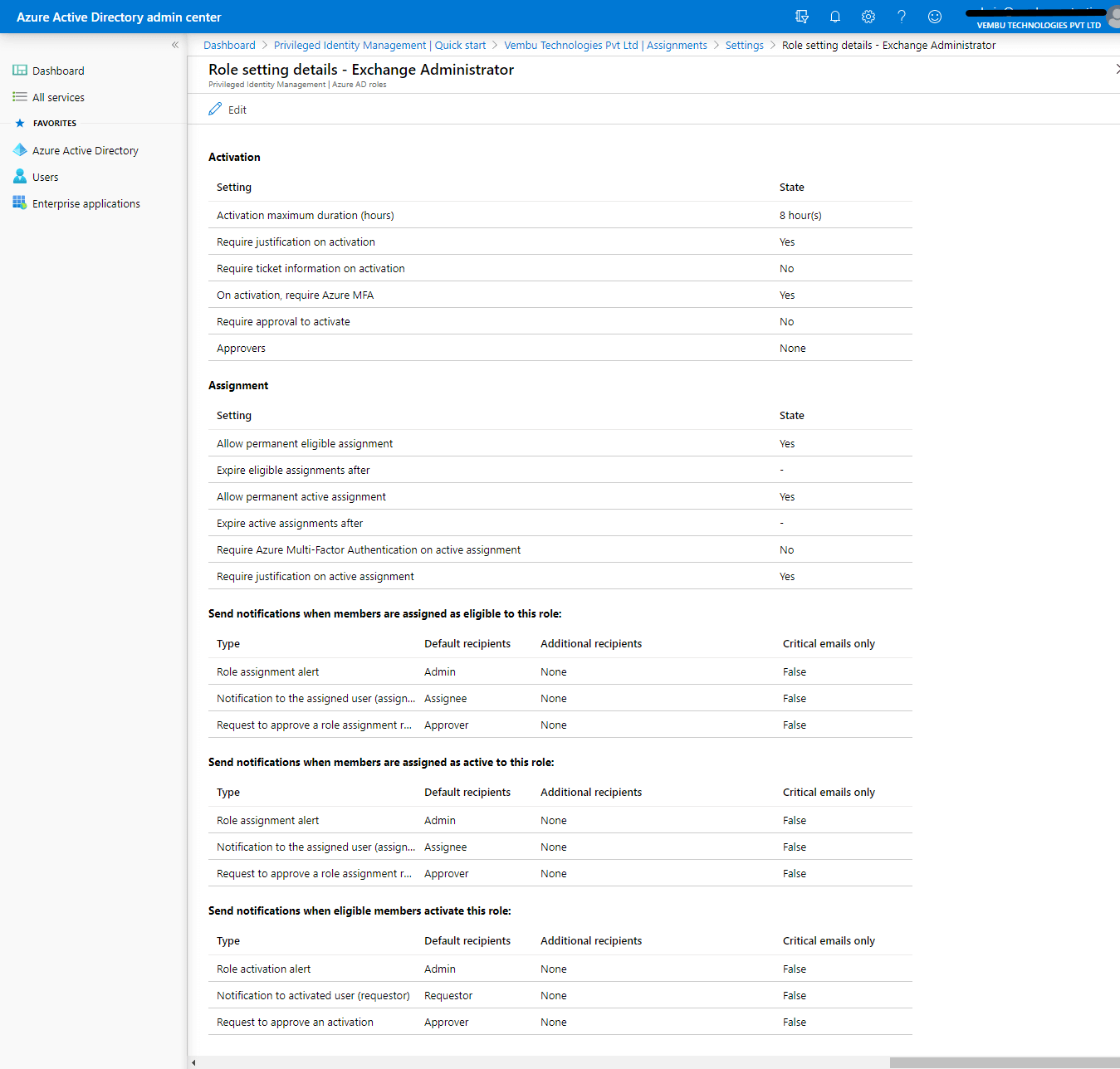
Activation settings
- Activation maximum duration ( in hours ) – Specify the number in hours
- Require justification on activation – Yes
- Require ticket information on activation – Yes / No
- On activation, require Azure MFA – Yes
- Require approval for activation – Yes / No
- Approvers – Global admin user or privileged admin role assigned user
Assignment settings –
- Allow permanent eligible assignment – Yes / No
- Expire eligible assignment after – Choose the end period
- Allow permanent active assignment – Yes / No
- Expire active assignment after – Choose the end period
- Require Azure MFA on active assignment – Yes / No
- Require justification on active assignment – Yes / No
Send notification settings
- Send notifications when members are assigned as eligible to this role:
- Send notifications when members are assigned as active to this role:
- Send notifications when eligible members activate this role:
A Global administrator can edit these settings for each role. In this example, an Exchange administrator role is provided.
Update:
In Jan 2023 Microsoft releases various new features across all Azure AD subscriptions. Of them few important features are listed here.
1. Cross-tenant synchronization – Microsoft document says ” Cross-tenant synchronization allows you to set up a scalable and automated solution for users to access applications across tenants in your organization. It builds upon the Azure AD B2B functionality and automates creating, updating, and deleting B2B users. Currently this feature is in Public preview mode.
2. Azure AD cloud sync new user experience – Microsoft released a new guided experience for syncing objects from AD to Azure AD using Azure AD Cloud Sync in Azure portal. With this new experience, Hybrid Identity Administrators can easily determine which sync engine to use for their scenarios and learn more about the various options they have with sync solutions. With a rich set of tutorials and videos, customers can learn everything about Azure AD cloud sync in one single place. Currently this feature is in public preview mode.
3. Support for Directory Extensions using Azure AD cloud sync – Hybrid IT Admins now can sync both Active Directory and Azure AD Directory Extensions using Azure AD Cloud Sync. This new capability is going to add the capability to dynamically discover the schema for both Active Directory and Azure AD, allowing customers to map the needed attributes using Cloud Sync’s attribute mapping experience. Currently this feature is in public preview mode.
Conclusion :
At these times, security breaches are common and occur every day. It is very important for an administrator to protect his Azure AD resources. Even a basic version of Azure AD is not sufficient considering the level of threats increasing day by day, and it’s becoming more and more important to protect resources with more than just a username and password. By implementing Azure AD Privileged Identity Management, organizations can protect their resources with improved security features and even keep an eye on what legitimate administrators are doing. And implementing Azure AD Identity protection allows administrators to detect potential vulnerabilities affecting any organization’s identities, configure automated responses, and investigate incidents.
Try out a free backup of your Microsoft 365 data to a storage medium of your choice, including Microsoft Azure Blob now.
Related Posts
Active Directory – Overview of Active Directory Files
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

